A Vulnerability Assessment Excel Template for Cybersecurity streamlines the process of identifying and prioritizing security weaknesses in systems and networks. This template allows cybersecurity professionals to systematically document vulnerabilities, track remediation efforts, and generate comprehensive reports. By organizing data efficiently, it enhances risk management and strengthens overall security posture.
Network Vulnerability Prioritization Excel Sheet
The
Network Vulnerability Prioritization Excel Sheet is a structured document designed to organize and rank security weaknesses within a network based on severity, exploitability, and potential impact. It helps cybersecurity professionals focus their remediation efforts on the most critical vulnerabilities first, optimizing resource allocation and reducing overall risk. By providing a clear, data-driven overview, this tool enhances decision-making and supports efficient vulnerability management in complex network environments.
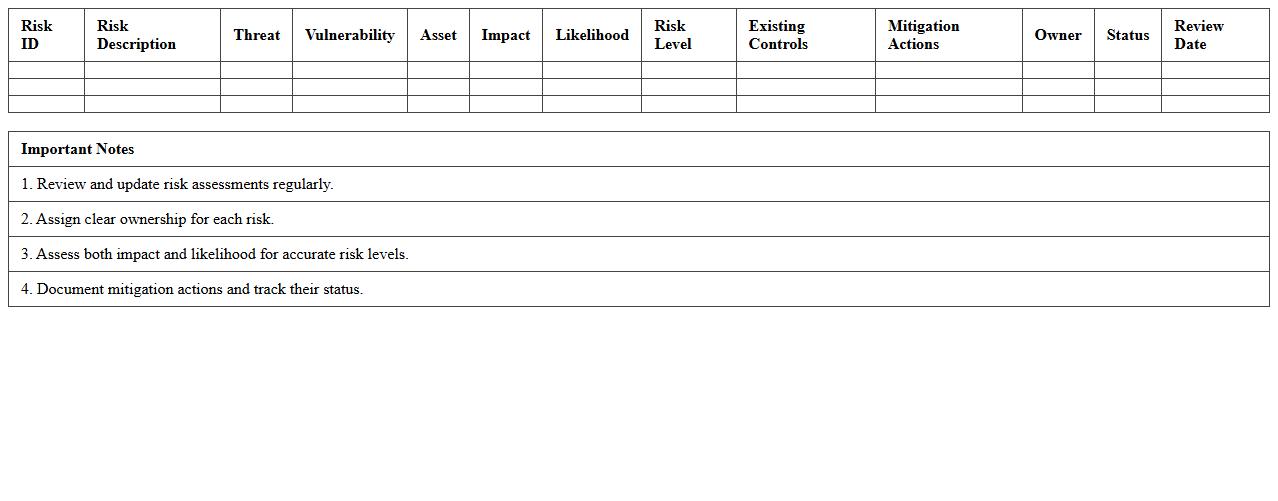
Cybersecurity Risk Assessment Matrix Template
A
Cybersecurity Risk Assessment Matrix Template document systematically categorizes potential cybersecurity threats based on their likelihood and impact, helping organizations prioritize risks effectively. By visually mapping vulnerabilities, it enables security teams to allocate resources strategically and implement targeted mitigation measures. This template is essential for maintaining robust defense mechanisms and ensuring proactive risk management in dynamic threat environments.
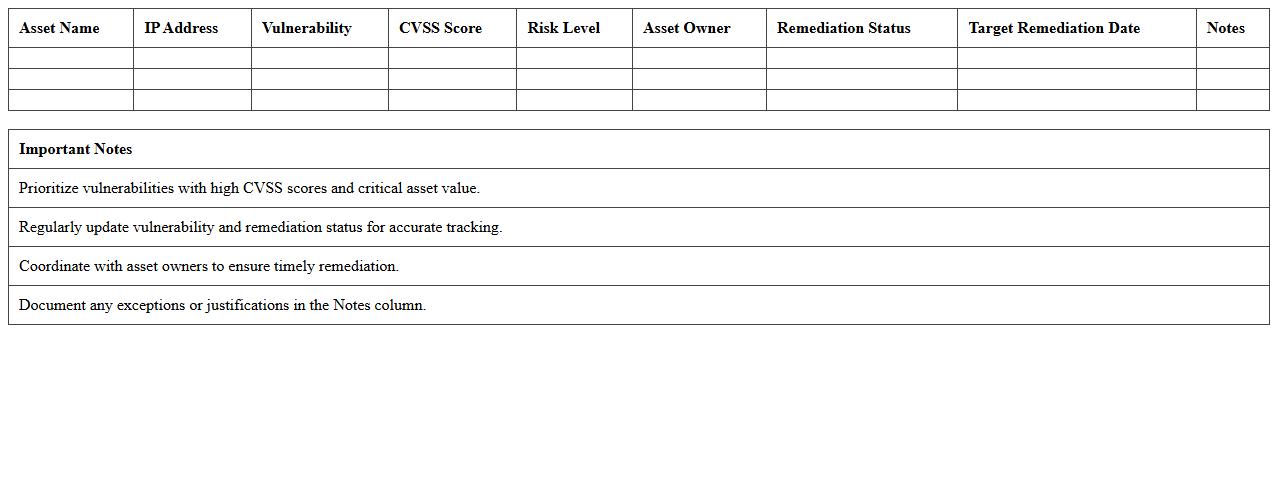
IT Asset Vulnerability Tracking Spreadsheet
An
IT Asset Vulnerability Tracking Spreadsheet document is a detailed tool used to monitor and manage security weaknesses in an organization's IT assets, such as hardware, software, and network components. This spreadsheet helps in systematically recording identified vulnerabilities, their severity levels, patch statuses, and remediation timelines, enabling proactive risk management. By providing a centralized view of asset vulnerabilities, it supports informed decision-making and prioritizes security efforts to protect critical infrastructure effectively.
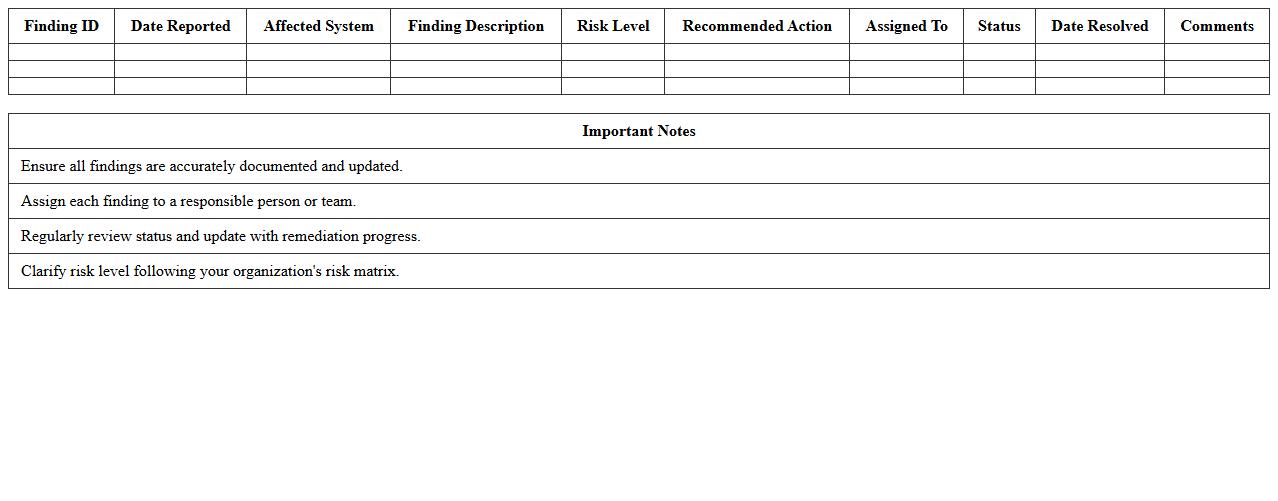
Penetration Test Findings Log Excel
A
Penetration Test Findings Log Excel document systematically records vulnerabilities, exploits, and security weaknesses identified during a penetration test. This organized log aids cybersecurity teams in prioritizing remediation efforts, tracking the status of each issue, and ensuring comprehensive coverage of all security gaps. It enhances communication among technical and management teams by providing a clear, concise overview of penetration test results for informed decision-making.
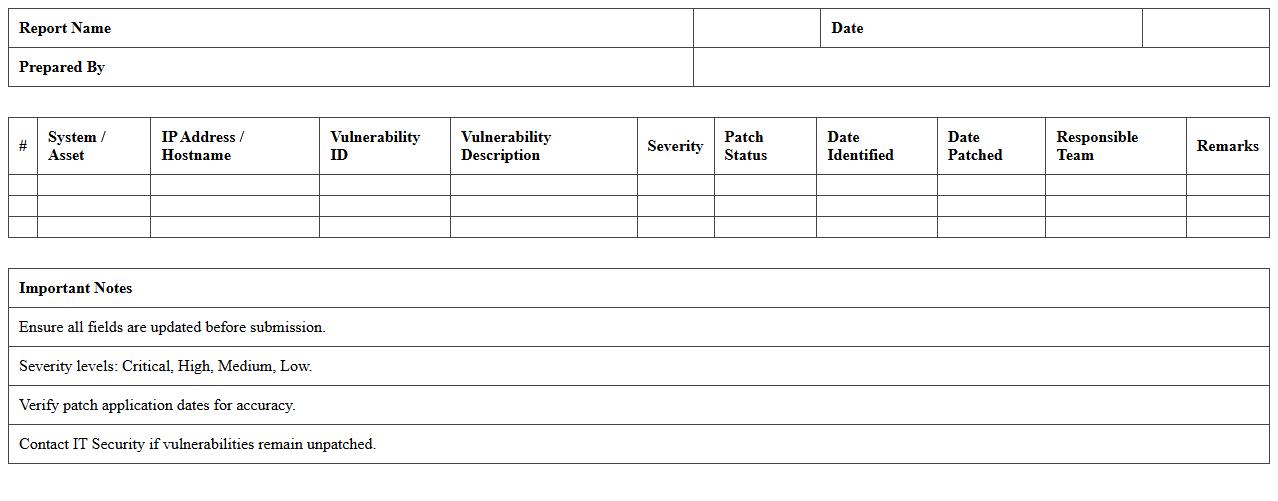
Patch Management Vulnerability Report Template
The
Patch Management Vulnerability Report Template document systematically tracks and evaluates software vulnerabilities and corresponding patches within an organization's IT systems. It consolidates detailed information on identified security gaps, patch statuses, and remediation timelines, enabling efficient prioritization of updates and risk reduction. Using this template enhances vulnerability management by providing clear, actionable insights that streamline compliance and strengthen overall cybersecurity posture.
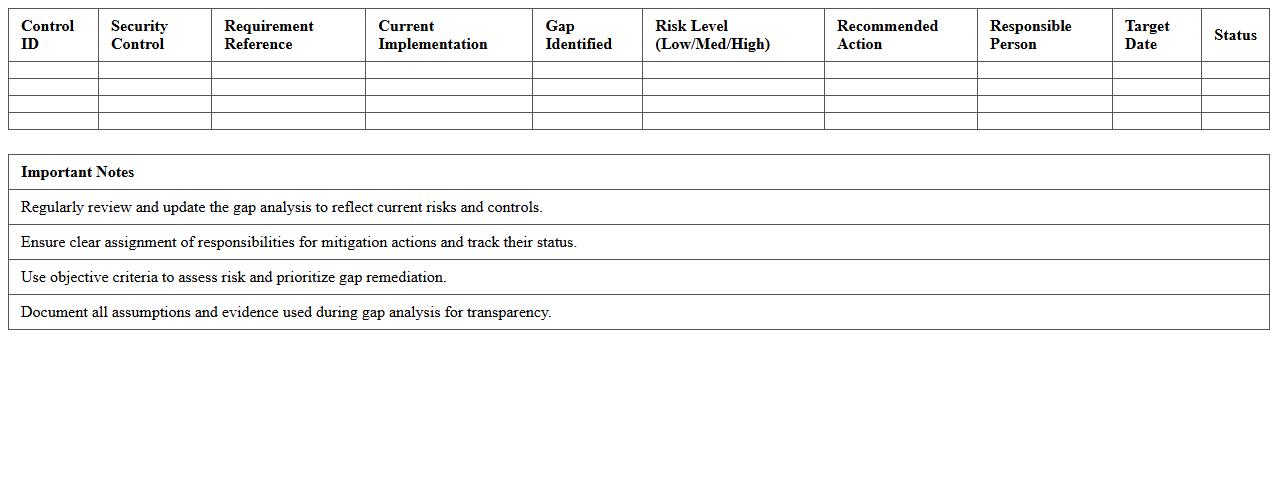
Security Control Gap Analysis Excel Sheet
A
Security Control Gap Analysis Excel Sheet is a structured document that helps organizations identify discrepancies between existing security measures and required compliance standards. It systematically catalogs security controls, highlights weaknesses, and tracks remediation efforts, enabling efficient risk management. Utilizing this tool ensures targeted improvements in cybersecurity posture, reducing vulnerabilities and enhancing overall information security governance.
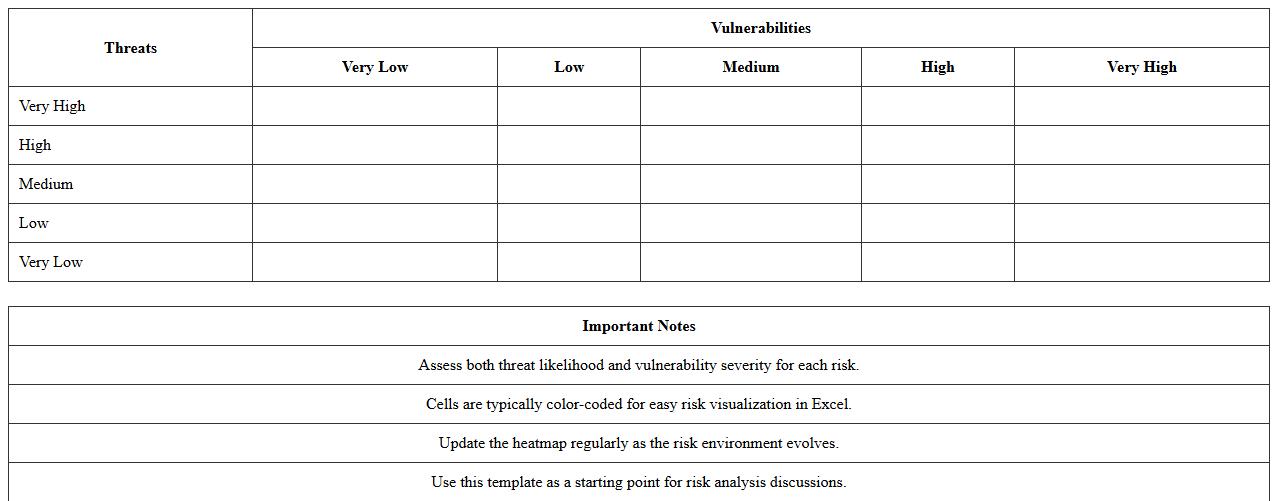
Threat and Vulnerability Heatmap Template
A
Threat and Vulnerability Heatmap Template document visually represents the severity and likelihood of potential security risks within an organization. It helps prioritize vulnerabilities by clearly categorizing them based on impact and probability, enabling informed decision-making for risk mitigation. This tool streamlines risk assessment processes and enhances cybersecurity strategy effectiveness by focusing efforts on high-risk areas.
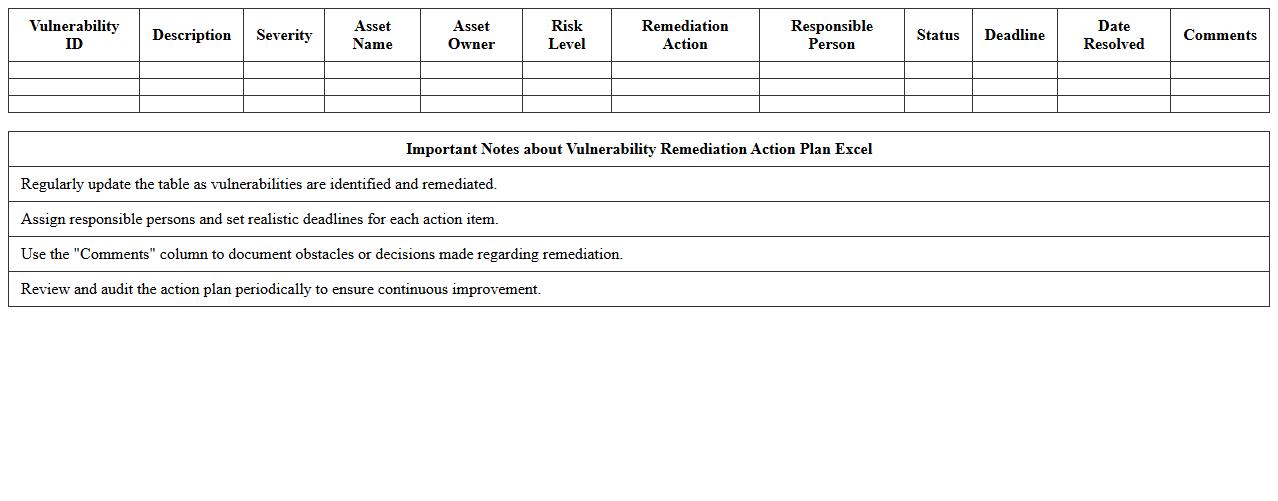
Vulnerability Remediation Action Plan Excel
A
Vulnerability Remediation Action Plan Excel document is a structured spreadsheet used to track, prioritize, and manage identified security vulnerabilities within an organization. It allows security teams to systematically document remediation tasks, assign responsibilities, and monitor progress to ensure timely resolution of risks. This tool enhances visibility, accountability, and efficiency in the vulnerability management process, ultimately strengthening the organization's security posture.
Web Application Vulnerability Assessment Tracker
A
Web Application Vulnerability Assessment Tracker document systematically records identified security weaknesses in web applications, categorizing them by severity, type, and remediation status. It enables development and security teams to monitor vulnerability trends, prioritize fixes, and ensure compliance with security standards. This organized approach enhances risk management, reduces potential exploits, and strengthens overall application security posture.
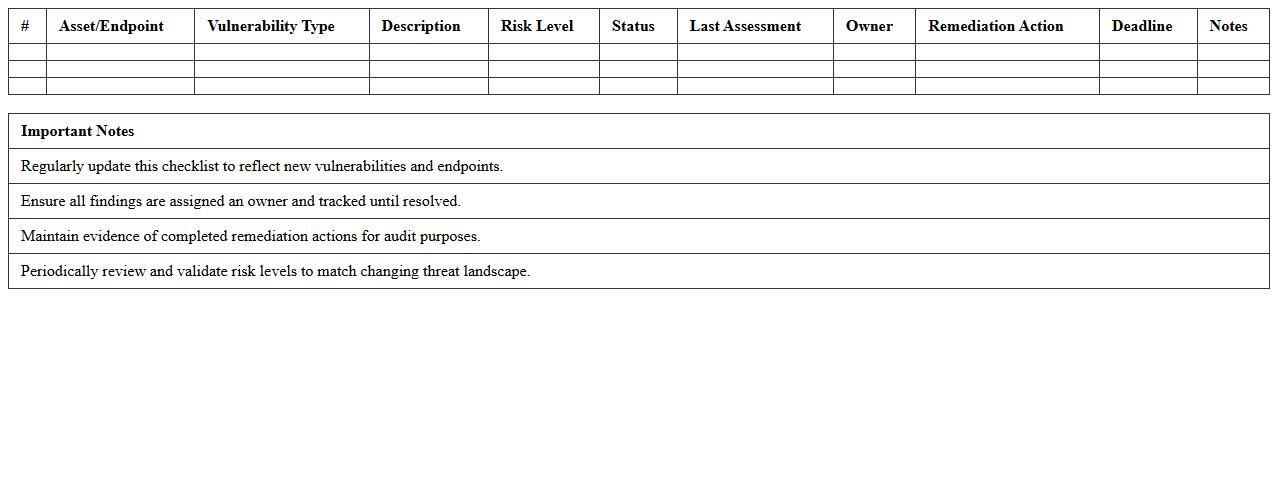
Endpoint Security Vulnerability Checklist Excel
The
Endpoint Security Vulnerability Checklist Excel document serves as a comprehensive tool to systematically identify, assess, and remediate security weaknesses across all endpoint devices in a network. It enables IT teams to track vulnerabilities, prioritize remediation tasks, and ensure compliance with security policies through a structured and easy-to-update format. Utilizing this checklist improves overall cybersecurity posture by reducing risks linked to endpoint exploits and facilitating proactive defense strategies.
How do you prioritize vulnerabilities in an Excel-based assessment matrix for cybersecurity?
Prioritizing vulnerabilities in an Excel-based matrix involves assigning risk scores based on severity, exploitability, and potential impact. Each vulnerability is evaluated using predefined criteria to calculate a comprehensive priority score. This enables security teams to focus remediation efforts on the most critical issues first.
What specific Excel formulas help automate CVSS score calculations in your document?
Automating CVSS score calculations in Excel can be done using the IF, AND, and VLOOKUP functions to interpret metric values and compute the overall score. By mapping qualitative metrics to numerical values, formulas aggregate these to output the CVSS base score automatically. This approach reduces manual errors and speeds up vulnerability scoring.
How is asset criticality weighted in your vulnerability assessment Excel sheet?
Asset criticality is weighted by assigning a numerical value based on its importance to business operations, often ranging from low to high. These weights are multiplied by the vulnerability risk scores to generate a weighted risk, reflecting both the vulnerability severity and asset value. This prioritization ensures that vulnerabilities on critical assets receive higher remediation focus.
What columns are essential for tracking remediation statuses in the Excel document?
Essential columns for remediation tracking include Status, Remediation Owner, Target Date, and Completion Date. These columns allow teams to monitor progress, assign responsibility, and document timelines for fixing vulnerabilities. Including notes for additional comments or blockers is also beneficial.
How do you link vulnerability findings with responsible owners in the spreadsheet?
Linking vulnerabilities with responsible owners is commonly done using a dedicated Owner column that contains names or team designations. Dropdown lists or data validation features ensure consistent assignment and prevent errors. By maintaining clear ownership, accountability is established, making follow-up and communication more efficient.
More Assessment Excel Templates