The Application Security Assessment Excel Template for Developers provides a structured framework to identify and analyze security vulnerabilities in software applications. It enables developers to systematically document potential risks, prioritize mitigation efforts, and track the progress of security improvements. This template enhances the efficiency of security reviews, ensuring comprehensive coverage of critical application components.
Threat Modeling Checklist Excel Template for Application Security
The
Threat Modeling Checklist Excel Template for Application Security is a structured document that helps identify, assess, and prioritize potential security threats in software development. It organizes security risks, mitigation strategies, and threat categories into an easily navigable spreadsheet, enhancing clarity and ensuring comprehensive coverage. This template streamlines the threat modeling process, making it easier to implement robust security controls and reduce vulnerabilities throughout the application lifecycle.
Secure Coding Practices Assessment Excel Sheet
The
Secure Coding Practices Assessment Excel Sheet is a structured tool designed to evaluate and ensure adherence to secure coding standards within software development projects. It systematically identifies potential security vulnerabilities by mapping coding practices against established security guidelines and best practices. This document is useful for developers and security teams to maintain consistent code quality, reduce risks of security breaches, and comply with regulatory requirements.
Web Application Vulnerability Matrix Spreadsheet
The
Web Application Vulnerability Matrix Spreadsheet is a comprehensive document that categorizes and prioritizes security vulnerabilities found in web applications, facilitating systematic risk assessment and management. It helps development and security teams track potential threats, assign remediation priorities, and ensure consistent application of security measures across projects. Utilizing this matrix improves the efficiency of vulnerability detection, enhances communication among stakeholders, and supports proactive protection against cyberattacks.
Developer Static Code Analysis Tracking Excel
A
Developer Static Code Analysis Tracking Excel document is a structured spreadsheet used to monitor and manage findings from static code analysis tools. It helps track code quality issues, vulnerabilities, and compliance with coding standards across development projects, enabling developers to prioritize fixes and improve software reliability. By systematically capturing and organizing analysis results, it enhances collaboration, accountability, and efficient resolution of code defects.
Application Penetration Testing Findings Log
The
Application Penetration Testing Findings Log is a detailed document that records identified vulnerabilities, security flaws, and potential exploitation methods discovered during a penetration test of an application. It serves as a critical reference for developers, security teams, and stakeholders to understand the specific weaknesses within the application environment. This log facilitates prioritization of remediation efforts, enhances security posture, and supports compliance with industry standards by providing a transparent record of security testing outcomes.
Security Patch Status Tracker Excel Template
The
Security Patch Status Tracker Excel Template is a comprehensive tool designed to monitor and manage the implementation of security patches across software and systems. It enables organizations to systematically track patch deployment dates, assess compliance status, and identify vulnerabilities that require urgent attention, enhancing overall cybersecurity posture. By providing a centralized and organized view of patch statuses, this template helps reduce the risk of security breaches and ensures timely updates to protect against emerging threats.
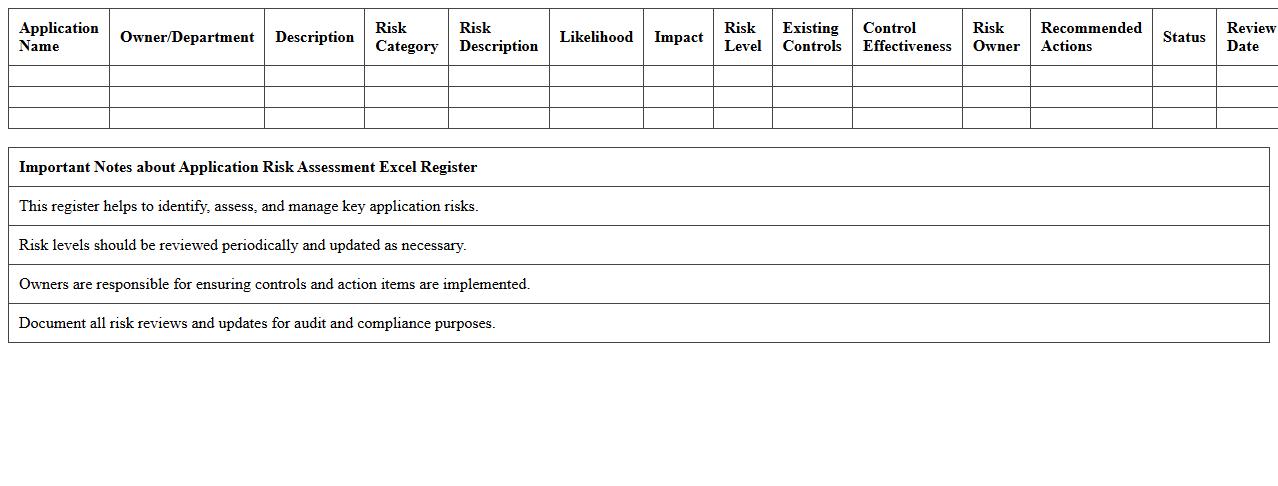
Application Risk Assessment Excel Register
The
Application Risk Assessment Excel Register document systematically captures and evaluates potential risks associated with software applications, enabling organizations to identify vulnerabilities and prioritize mitigation efforts. By organizing risk data, impact ratings, and control measures in a structured format, it enhances decision-making and supports compliance with regulatory requirements. This tool is essential for maintaining application security, minimizing operational disruptions, and safeguarding sensitive information effectively.
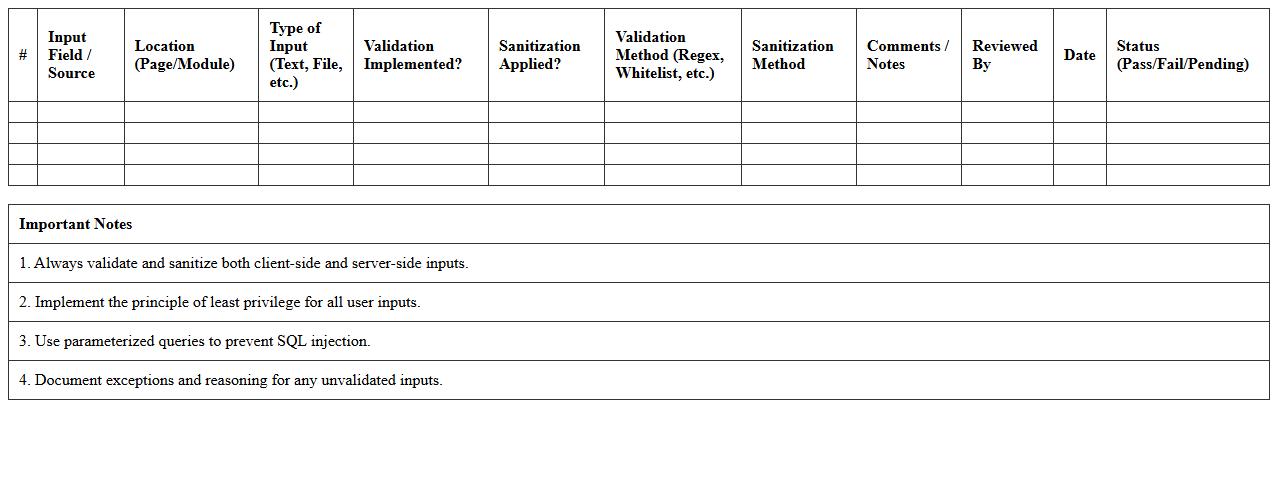
Input Validation & Sanitization Audit Spreadsheet
The
Input Validation & Sanitization Audit Spreadsheet document systematically tracks and evaluates the processes used to validate and sanitize user inputs in software applications. It helps identify vulnerabilities related to improper data handling, reducing risks of security breaches such as SQL injection and cross-site scripting attacks. This audit tool ensures compliance with security standards and enhances the overall robustness of data integrity measures in development projects.
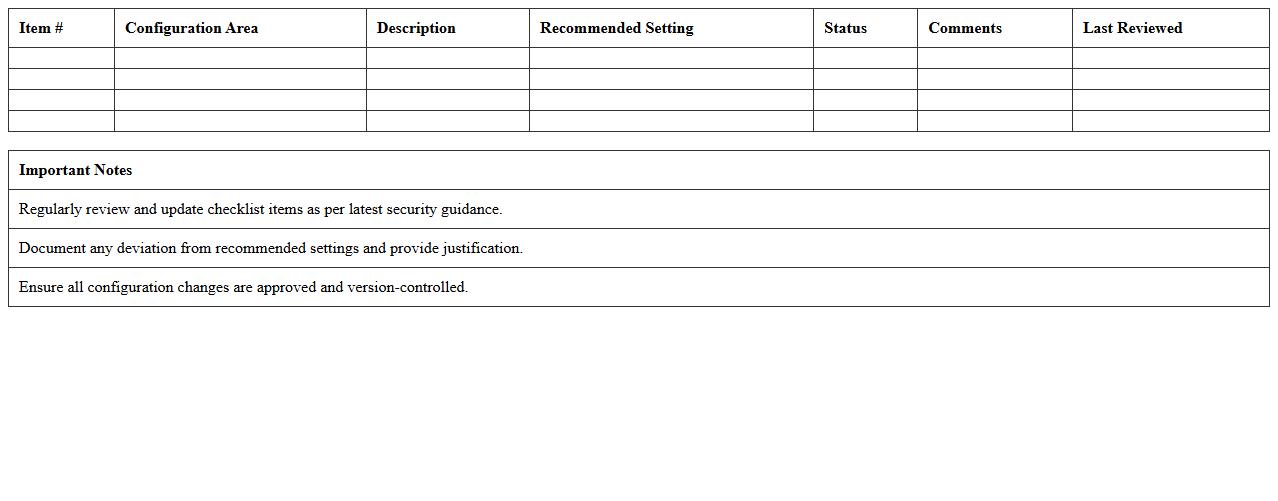
Secure Configuration Checklist Excel Template
The
Secure Configuration Checklist Excel Template document is a structured tool designed to help organizations systematically verify and maintain secure system settings. It enables tracking of compliance with security policies by listing essential configuration parameters and their desired states. Using this template enhances risk management by ensuring consistent application of security standards across devices and environments.
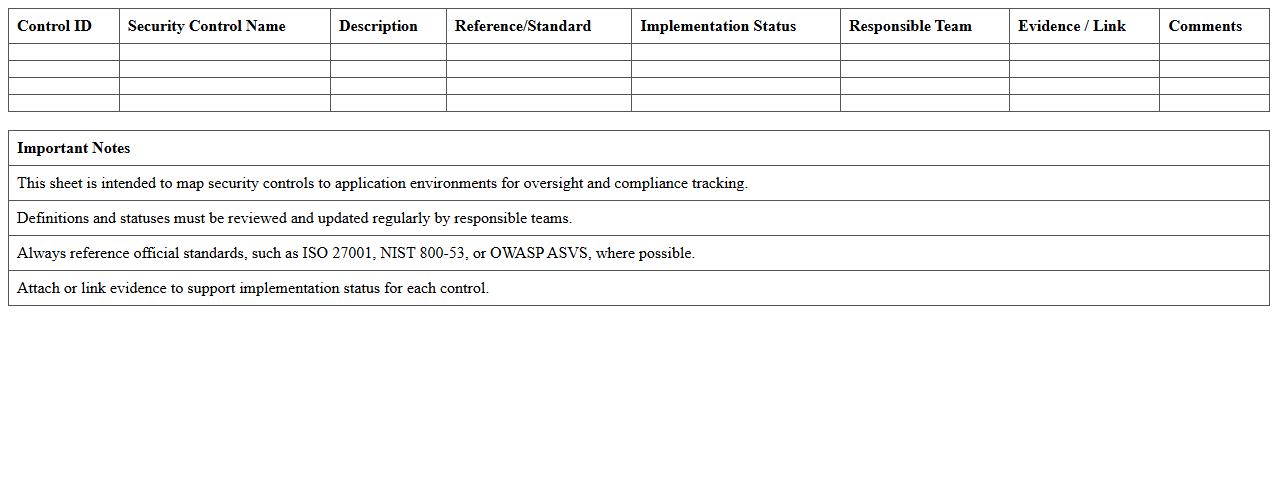
Application Security Controls Mapping Sheet
The
Application Security Controls Mapping Sheet document systematically aligns security controls with application components and relevant standards, ensuring comprehensive coverage of security requirements. It is useful for identifying gaps, streamlining audits, and facilitating compliance with industry regulations such as OWASP, NIST, and ISO 27001. This mapping enhances risk management by providing clear visibility into implemented controls and their effectiveness in protecting sensitive data and application integrity.
How does the Application Security Assessment Excel address OWASP Top 10 vulnerabilities for developers?
The Application Security Assessment Excel is meticulously designed to map directly to the OWASP Top 10 vulnerabilities, ensuring developers can quickly identify critical security flaws. Each worksheet itemizes common risks such as Injection, Broken Authentication, and Cross-Site Scripting, providing clear definitions and examples. This structured approach helps developers prioritize remediation by understanding the impact and prevalence of these vulnerabilities within their applications.
Which columns in the Excel focus on secure coding practices for input validation?
The Excel template includes dedicated columns such as Input Type, Validation Method, and Sanitization Technique that emphasize secure coding practices for input validation. These columns guide developers to document how data inputs are checked and cleaned before processing. This focus ensures that vulnerabilities related to improper input handling, like Injection flaws, are systematically addressed.
How is risk scoring for identified vulnerabilities automated within the spreadsheet?
Risk scoring in the spreadsheet is automated using predefined formulas that calculate scores based on severity, likelihood, and exploitability factors. The template integrates a weighted scoring system that updates dynamically as developers input details about each vulnerability. This automation enables a consistent and objective risk assessment process, helping teams focus on the most critical security issues.
What developer-specific remediation guidance is included in the Excel template?
The Excel template provides tailored remediation steps categorized by vulnerability type, offering developer-specific guidance to fix each issue effectively. It includes best practices, code examples, and references to standards such as secure coding libraries and frameworks. This practical advice supports developers in implementing fixes that are aligned with industry security requirements.
How can version control for security assessment entries be managed in the document?
Version control is facilitated through columns dedicated to revision date, author, and change description, allowing teams to track modifications to security assessment entries. When used in conjunction with tools like SharePoint or Git, the Excel file's integrity and history can be maintained efficiently. This approach ensures accountability and traceability throughout the security assessment lifecycle.
More Assessment Excel Templates