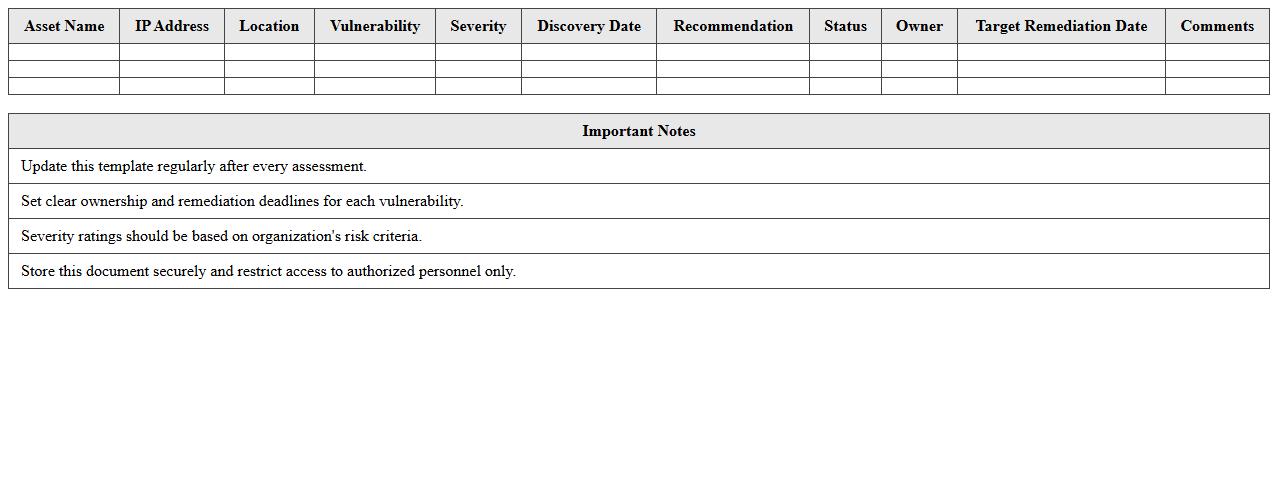
Network Vulnerability Assessment Excel Template
A
Network Vulnerability Assessment Excel Template document is a structured tool designed to systematically identify, document, and analyze security weaknesses within a network infrastructure. It helps IT professionals organize vulnerability data, prioritize risks based on severity, and plan appropriate remediation actions efficiently. Using this template enhances the accuracy and consistency of assessments, improving overall network security management and compliance tracking.
IT Asset Security Audit Excel Template
The
IT Asset Security Audit Excel Template is a structured document designed to systematically track and evaluate the security status of IT assets within an organization. It enables efficient identification of vulnerabilities, compliance gaps, and risk levels for hardware, software, and network components. Using this template streamlines audit processes, ensures accurate asset documentation, and supports informed decision-making for enhancing cybersecurity measures.
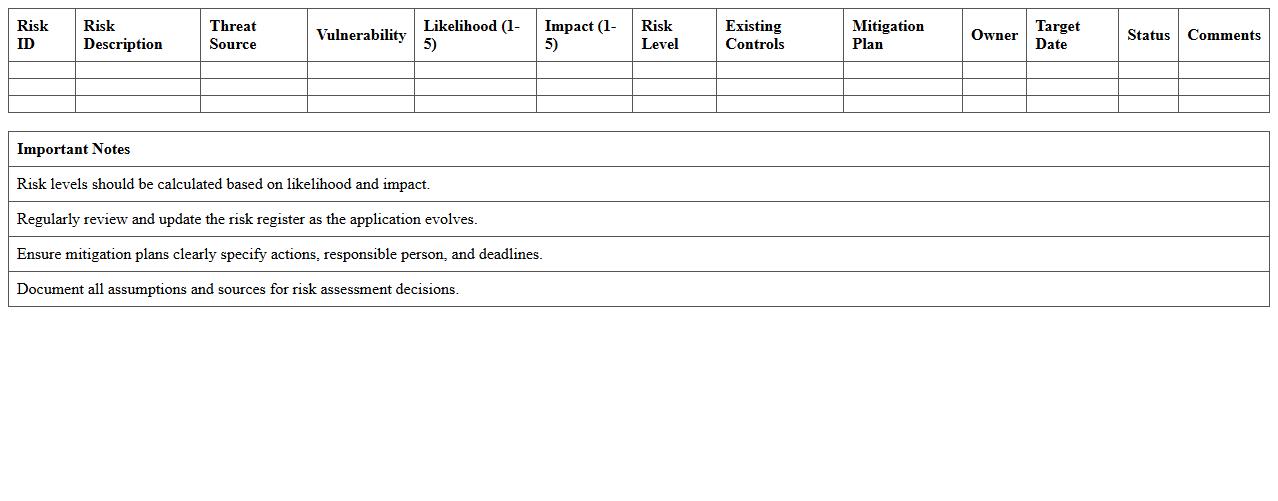
Application Security Risk Assessment Excel Template
The
Application Security Risk Assessment Excel Template document provides a structured framework to identify, evaluate, and prioritize security vulnerabilities within software applications. This template enables organizations to systematically document potential threats, assess their impact and likelihood, and develop mitigation strategies to enhance overall security posture. Utilizing this tool streamlines risk management efforts, ensures comprehensive coverage of security concerns, and facilitates informed decision-making for protecting critical application assets.
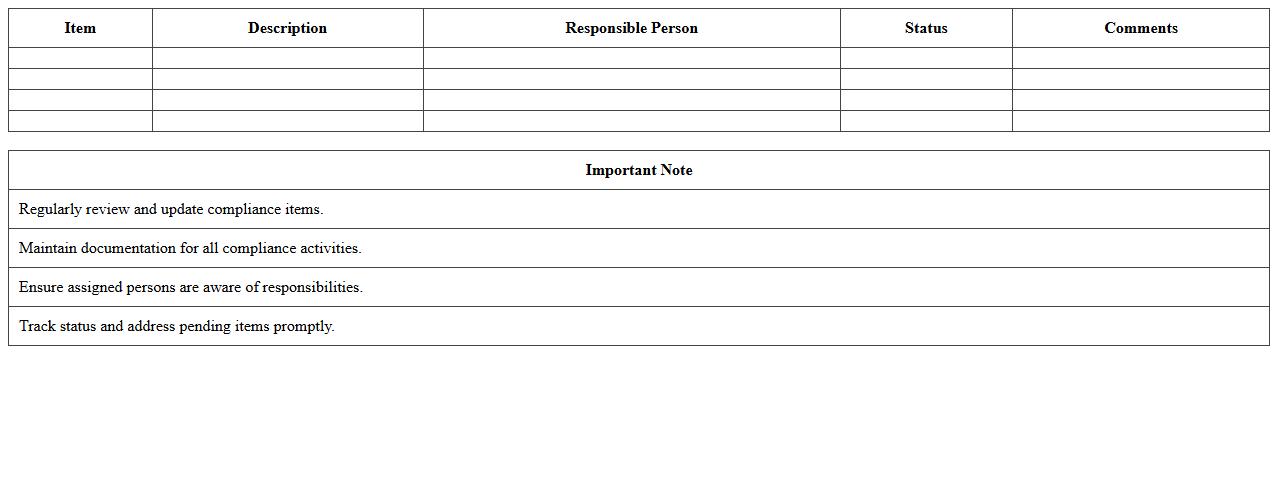
IT Compliance Checklist Excel Template
The
IT Compliance Checklist Excel Template is a structured document designed to help organizations systematically track and manage their adherence to IT regulations, standards, and policies. It enables businesses to identify compliance gaps, ensure regulatory requirements are met, and maintain cybersecurity protocols efficiently. This template enhances audit preparedness and reduces risks by providing a clear, organized overview of compliance status within an easily accessible spreadsheet format.
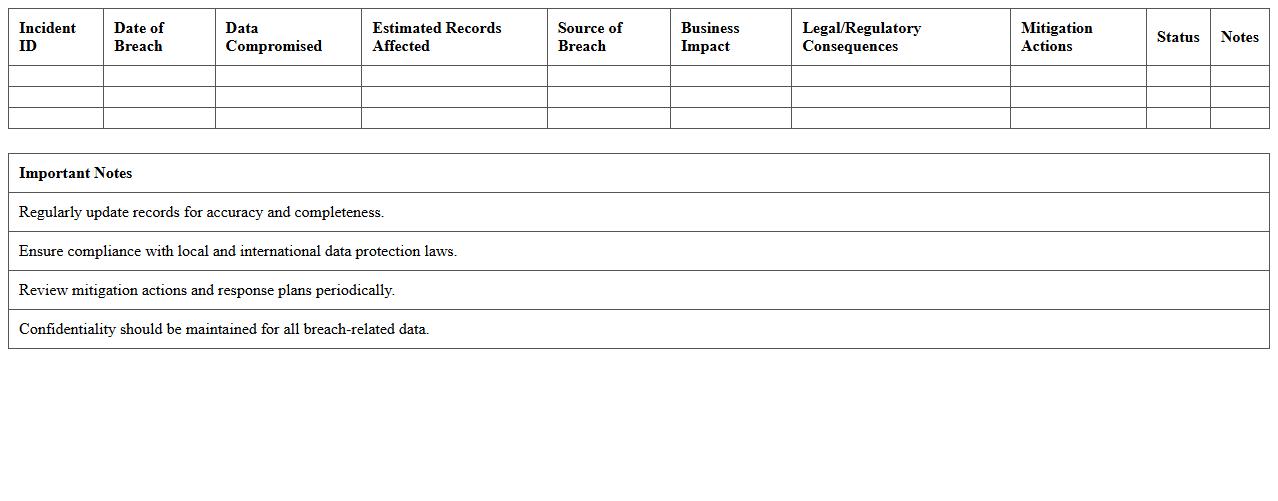
Data Breach Impact Analysis Excel Template
The
Data Breach Impact Analysis Excel Template is a structured tool designed to systematically assess and quantify the consequences of data breaches on an organization. It enables users to identify affected data types, evaluate financial losses, regulatory fines, and reputational damage by organizing inputs into clear, analyzable formats. This template aids cybersecurity teams and risk managers in prioritizing mitigation efforts and making informed decisions to minimize future breach impacts.
Endpoint Security Evaluation Excel Template
The
Endpoint Security Evaluation Excel Template document is a structured tool designed to assess and compare the security measures implemented across various endpoints within a network. It helps organizations systematically evaluate factors such as antivirus protection, firewall status, patch management, and threat detection capabilities, enabling easier identification of vulnerabilities. This template streamlines the security review process, supports informed decision-making, and enhances overall endpoint protection strategy.
Information Security GAP Analysis Excel Template
An
Information Security GAP Analysis Excel Template is a structured tool designed to identify discrepancies between current security practices and desired information security standards. It enables organizations to systematically evaluate vulnerabilities, compliance weaknesses, and areas needing improvement by comparing existing controls against benchmarks such as ISO 27001 or NIST frameworks. This template streamlines the assessment process, allowing for clear documentation, prioritization of risks, and creation of actionable plans to enhance overall security posture.
User Access Rights Review Excel Template
The
User Access Rights Review Excel Template document is a structured tool designed to help organizations systematically evaluate and manage user permissions across various systems. It enables efficient tracking of access levels, ensuring compliance with security policies and minimizing risks associated with unauthorized access. This template supports periodic reviews by providing clear visibility into user roles and privileges, facilitating timely identification and remediation of potential access discrepancies.
IT Security Incident Log Excel Template
The
IT Security Incident Log Excel Template is a structured document designed to systematically record and track security incidents within an organization. It helps in documenting critical details such as incident type, date, severity, status, and resolution steps, enabling efficient monitoring and analysis of security breaches. This template enhances incident response by providing clear, organized data that supports compliance audits, trend identification, and improved cybersecurity strategies.
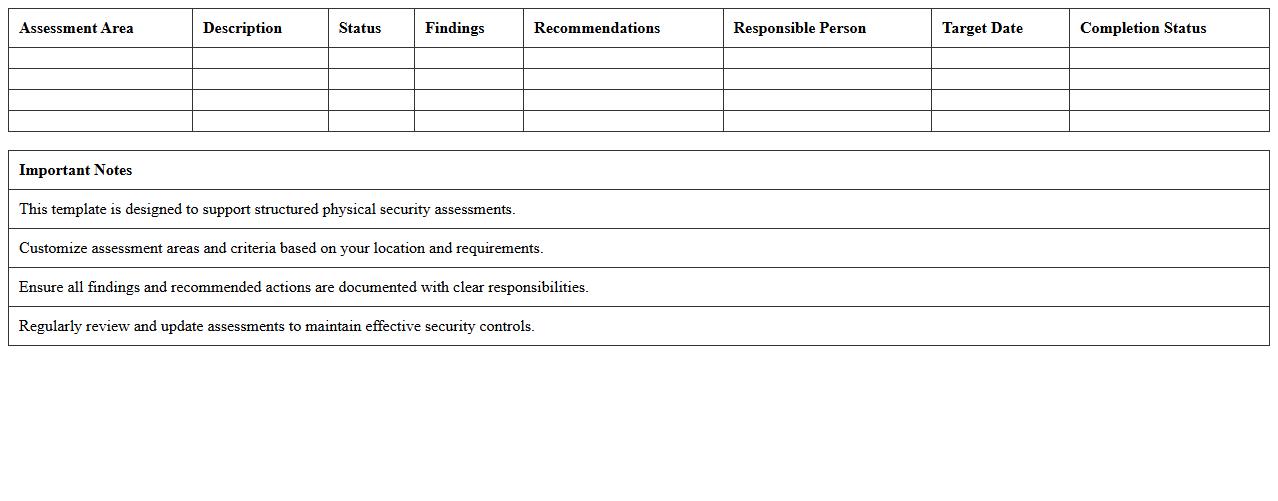
Physical Security Assessment Excel Template
The
Physical Security Assessment Excel Template document systematically evaluates vulnerabilities in a facility's physical security measures by organizing data on entry points, surveillance systems, and access control protocols. It aids security professionals in identifying risks, tracking security improvements, and ensuring compliance with safety standards. This structured approach enhances decision-making, reduces potential threats, and supports the implementation of effective security strategies.
Specific Access Controls for Sensitive Data
The Security Assessment Excel meticulously documents access controls for sensitive data by specifying user roles and permissions. It ensures only authorized personnel can access critical information, minimizing the risk of data breaches. The document also includes multi-factor authentication and data encryption as part of its control measures.
Tracking Remediation Status of IT Security Vulnerabilities
The Excel sheet employs a detailed tracking system for the remediation status of identified vulnerabilities, categorizing them as open, in progress, or closed. Each issue is assigned a deadline and owner to enhance accountability. This structured approach facilitates timely resolution and continuous security improvement.
Inclusion and Categorization of Third-Party Risk Assessments
Third-party risk assessments are comprehensively included within the document, highlighting vendor risks and their impact on overall security posture. These assessments are categorized by risk severity and compliance status. The document ensures ongoing monitoring and risk mitigation strategies for third-party interactions.
Recommended Frequency of Security Audits for IT Systems
The Excel recommends conducting security audits on a quarterly or bi-annual basis to maintain robust IT system defenses. Regular audits help identify new vulnerabilities and verify compliance with policies. The frequency recorded ensures that audits are performed consistently to reduce risk exposure.
Referenced Encryption Standards in the Assessment
The assessment documentation references industry-recognized encryption standards such as AES-256 and TLS 1.2 or above. These standards guarantee data confidentiality and integrity during storage and transmission. Compliance with these encryption protocols is mandated for securing sensitive information effectively.