The IT Security Audit Checklist Excel Template for Startups provides a comprehensive and easy-to-use framework to assess your company's cybersecurity measures. It helps identify vulnerabilities, ensure compliance with industry standards, and implement best practices tailored for startup environments. This template streamlines the auditing process, allowing startups to safeguard their digital assets efficiently.
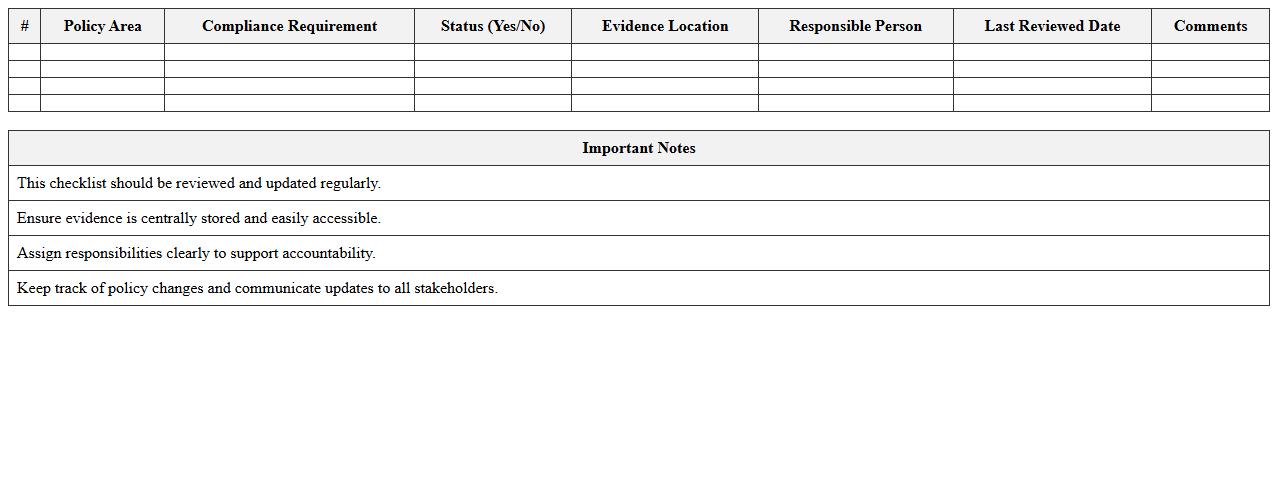
IT Security Policy Compliance Checklist Excel Template
The
IT Security Policy Compliance Checklist Excel Template document is a structured tool designed to help organizations systematically verify adherence to established IT security policies. It allows tracking of compliance status, identifying gaps, and ensuring all security measures are consistently applied across the IT infrastructure. Using this template enhances risk management, supports audits, and promotes a culture of security awareness within the organization.
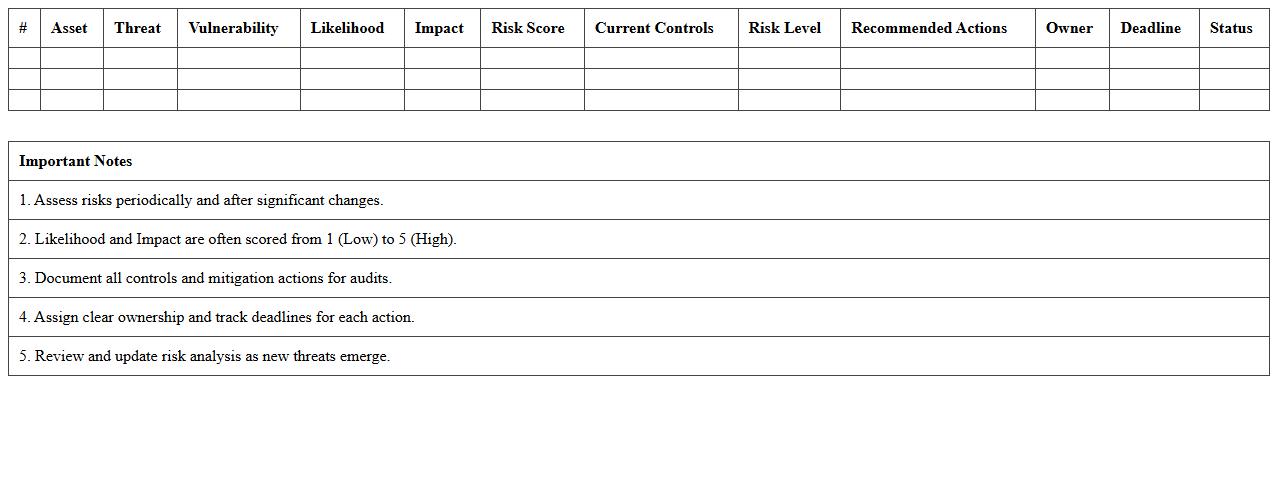
Network Security Assessment Excel Template
The
Network Security Assessment Excel Template document is a structured tool designed to systematically evaluate the security posture of a network by identifying vulnerabilities, assessing risks, and documenting mitigation strategies. It helps IT professionals and cybersecurity teams streamline the analysis process by providing predefined categories, risk scoring, and comprehensive checklists. This template enhances decision-making efficiency, improves compliance tracking, and supports proactive security improvements within an organization.
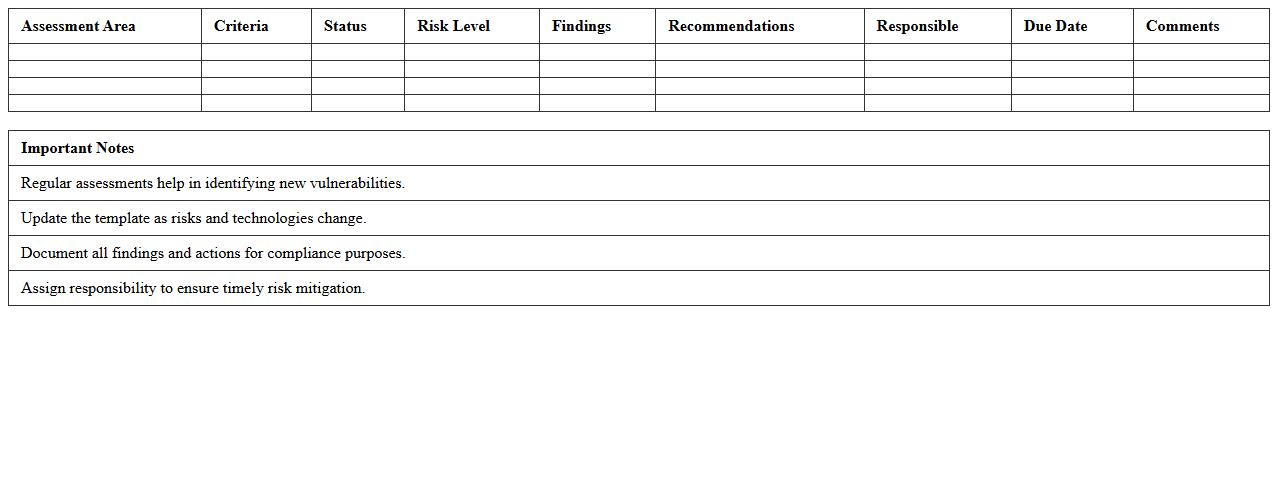
Cybersecurity Risk Analysis Excel Template
A
Cybersecurity Risk Analysis Excel Template document provides a structured framework to identify, assess, and prioritize potential cyber threats and vulnerabilities within an organization's IT infrastructure. This tool simplifies the complex process of evaluating risks by allowing users to input data, calculate risk levels, and generate actionable insights for improving security measures. It is useful for enhancing decision-making, allocating resources effectively, and maintaining compliance with industry regulations.
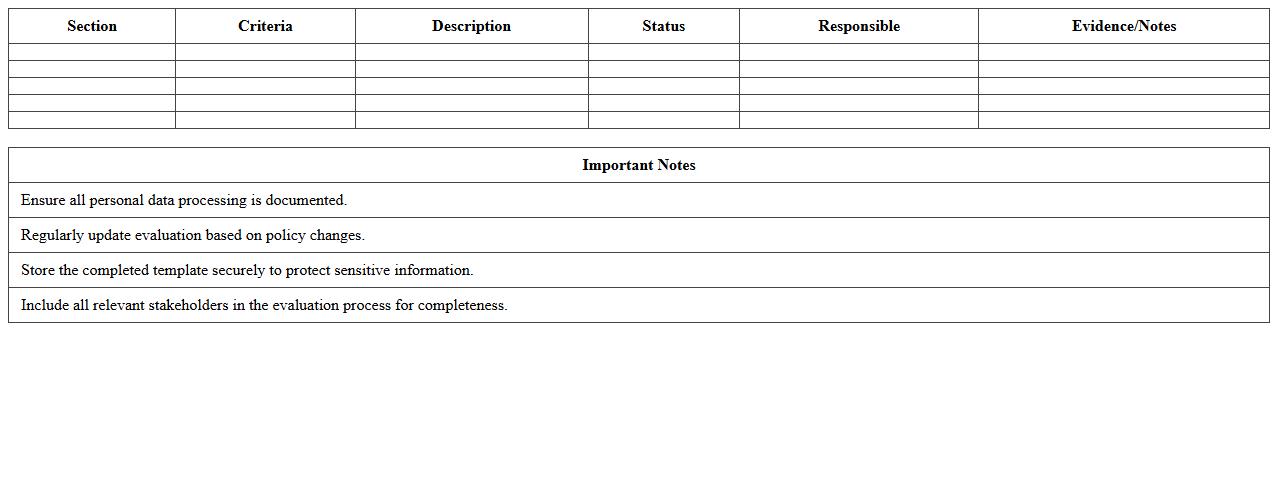
Data Protection Evaluation Excel Template
The
Data Protection Evaluation Excel Template document serves as a comprehensive tool designed to assess and monitor compliance with data protection regulations such as GDPR and CCPA. By systematically evaluating data handling practices, risk levels, and security measures, this template enables organizations to identify vulnerabilities and implement corrective actions efficiently. Using this structured approach enhances data privacy management, reduces the risk of breaches, and ensures adherence to legal standards.
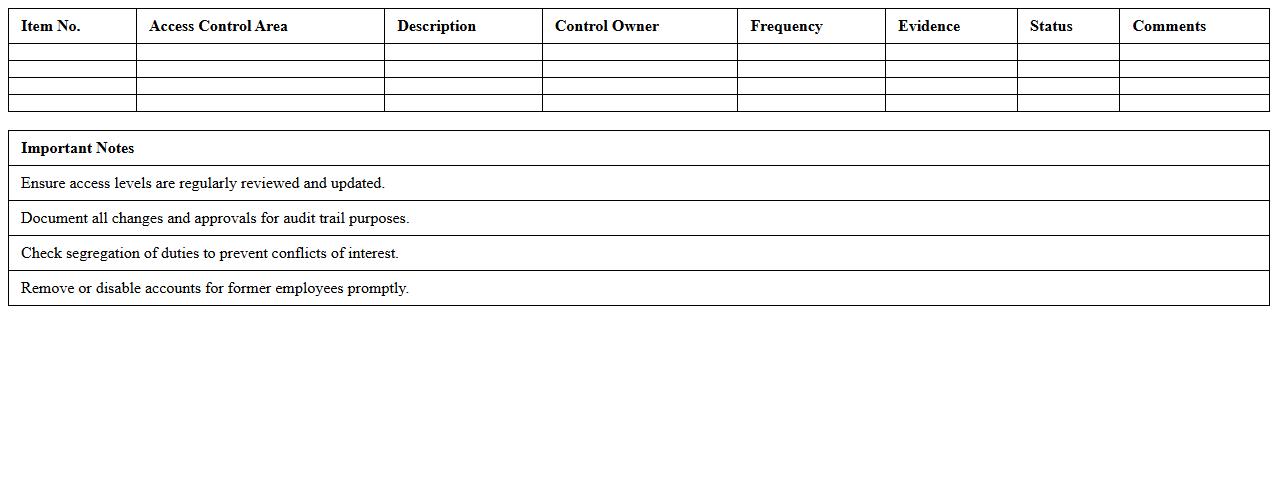
Access Control Audit Excel Template
The
Access Control Audit Excel Template document is a comprehensive tool designed to systematically evaluate and document access permissions within an organization. It helps identify unauthorized access, streamline permission management, and ensure compliance with security policies and regulatory requirements. By consolidating access data into an organized format, this template enhances audit efficiency and supports proactive risk mitigation.
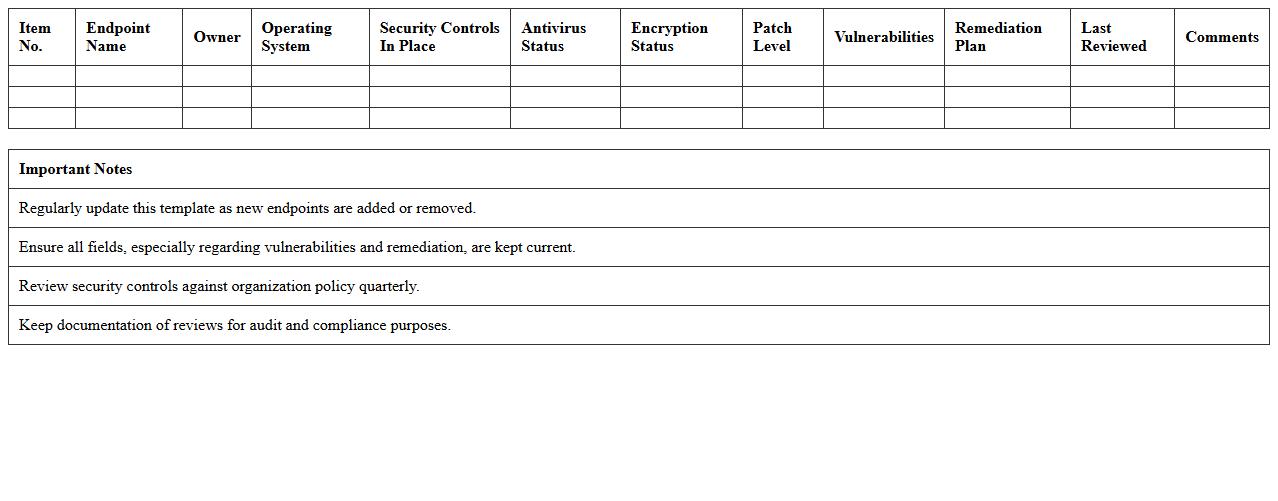
Endpoint Security Review Excel Template
The
Endpoint Security Review Excel Template document is a structured tool designed to systematically assess and monitor the security posture of endpoint devices within an organization. It helps identify vulnerabilities, track compliance with security policies, and prioritize remediation efforts by organizing critical data in a clear, actionable format. Using this template enhances visibility into endpoint risks, enabling effective decision-making and strengthening overall cybersecurity defenses.
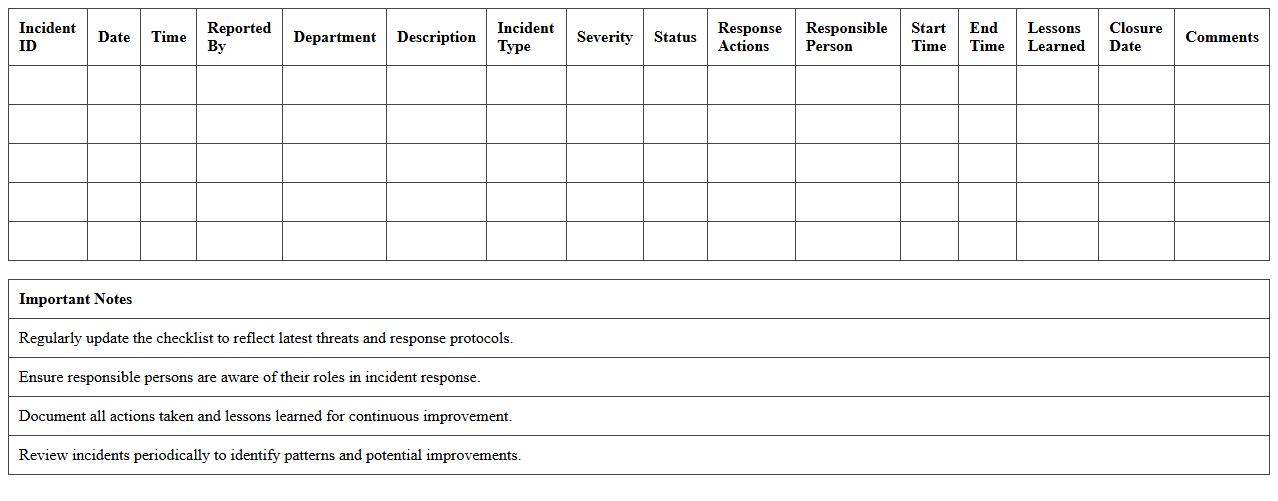
Security Incident Response Checklist Excel Template
A
Security Incident Response Checklist Excel Template is a structured document designed to guide teams through the systematic handling of security breaches and cyber threats. It organizes critical steps, such as detection, containment, eradication, recovery, and post-incident analysis, ensuring no phase is overlooked during an incident. This template enhances response efficiency, promotes consistency, and helps maintain compliance with security standards by providing a clear, actionable framework for incident management.
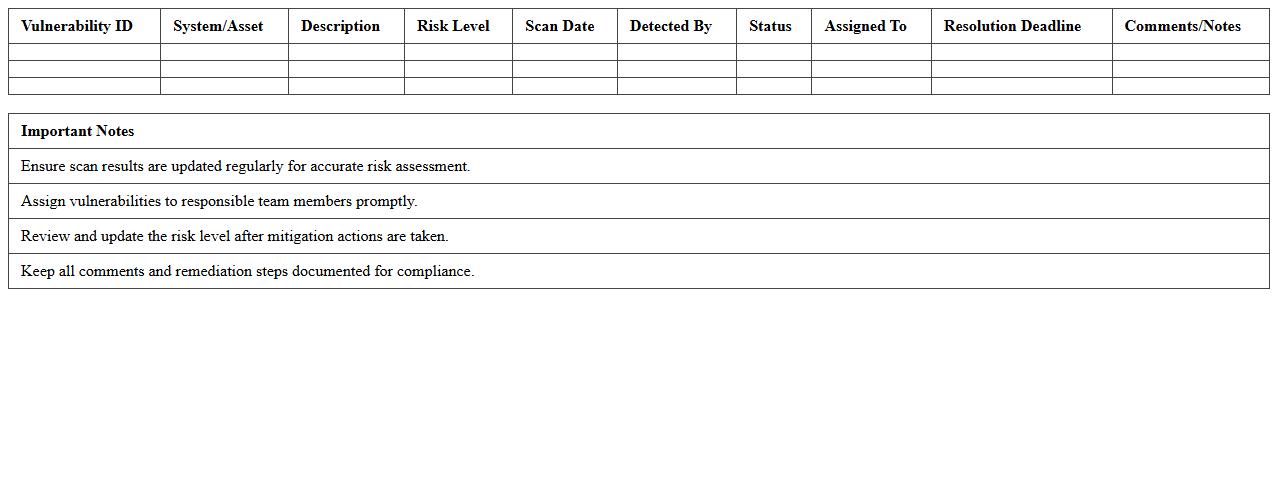
Startup IT System Vulnerability Scan Excel Template
The
Startup IT System Vulnerability Scan Excel Template is a structured document designed to identify and track potential security weaknesses within an IT infrastructure. It allows startups to systematically assess vulnerabilities, categorize risks, and prioritize remediation efforts with clear, organized data representation. Using this template enhances security management efficiency, ensuring critical threats are addressed promptly to protect sensitive information and maintain operational integrity.
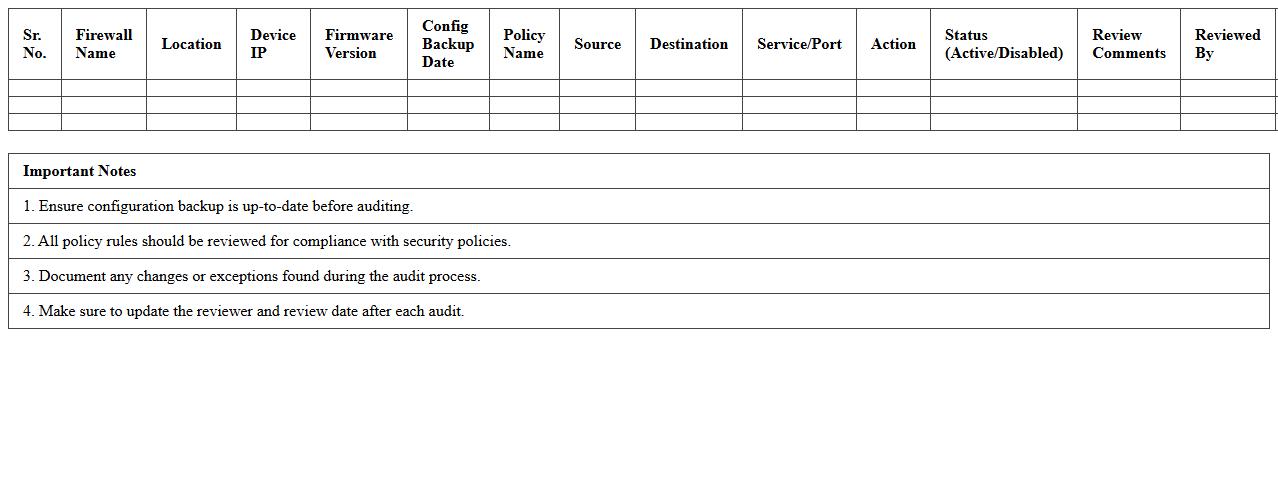
Firewall Configuration Audit Excel Template
The
Firewall Configuration Audit Excel Template document serves as a comprehensive tool for systematically reviewing and verifying firewall settings to ensure compliance with security policies. It helps identify misconfigurations, vulnerabilities, and unauthorized rule changes by organizing firewall rules, policies, and logs into a structured format. Utilizing this template enhances network security by enabling consistent audits, reducing risks, and improving the management of firewall configurations across IT infrastructures.
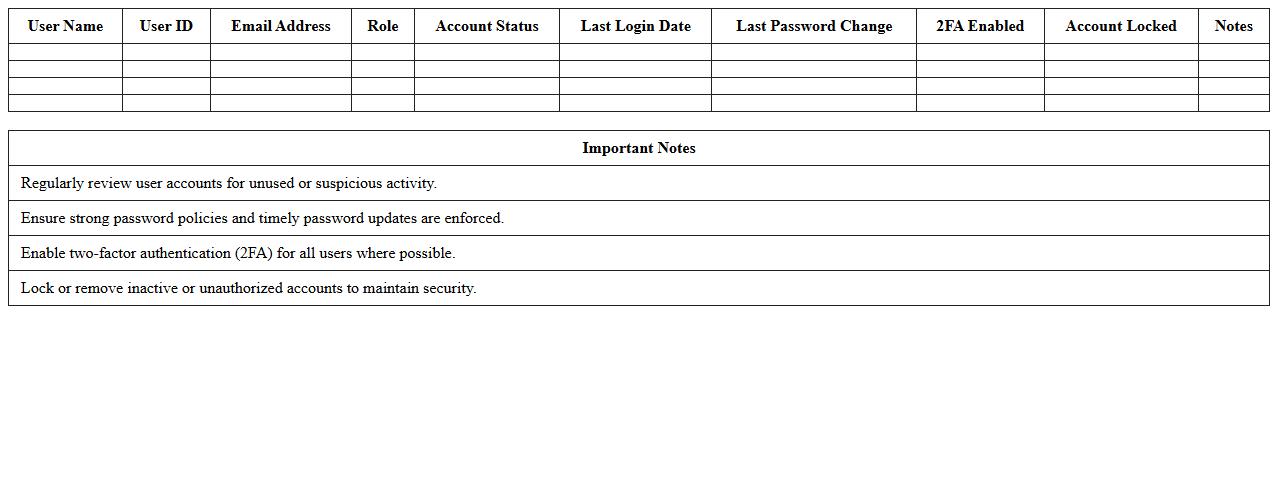
User Account Security Audit Excel Template
The
User Account Security Audit Excel Template is a comprehensive tool designed to systematically evaluate and monitor the security status of user accounts within an organization. It helps identify vulnerabilities such as weak passwords, inactive accounts, and unauthorized access, enabling IT teams to enforce security policies effectively. Utilizing this template improves compliance with security standards and reduces the risk of data breaches by maintaining a structured overview of account activities and permissions.
What key IT policies should be included in the Excel checklist for startup audits?
The Excel checklist for startup audits must include IT security policies to ensure asset protection and risk management. It should cover password protocols, incident response plans, and acceptable use policies. Including these policies helps maintain compliance and supports a strong IT governance framework.
How does your checklist address cloud service security controls?
Our checklist incorporates specific cloud service security controls such as data access permissions, encryption status, and compliance with industry standards. It ensures startups verify secure configurations and continuous monitoring of their cloud infrastructure. This reduces vulnerabilities linked to cloud-based services and enhances data protection.
Which access management items are tracked in your Excel template?
The Excel template tracks critical access management items including user access rights, role assignments, and multi-factor authentication status. It also monitors periodic access reviews to prevent unauthorized access. These measures help enforce security policies and mitigate internal threats.
Are third-party vendor risks outlined in your IT audit Excel sheet?
Yes, the checklist outlines third-party vendor risks by including vendor assessment status, contract compliance, and security controls review. This enables startups to identify potential risks arising from external partnerships. Proper management of these risks safeguards the organization's data integrity and reputation.
Does your checklist include data encryption and backup verification columns?
The checklist features columns for data encryption status and backup verification to ensure critical data is protected against unauthorized access and loss. It verifies if encryption protocols meet required standards and if backups are performed regularly. This is essential for business continuity and disaster recovery planning.
More Audit Excel Templates