Sure! Here are 10 semantic-optimized Excel template titles that are subsets of "Vulnerability Assessment Excel Template for Cybersecurity Firms":
A
Vulnerability Assessment Excel Template for cybersecurity firms systematically organizes and evaluates security weaknesses within IT infrastructures, enabling efficient risk identification and mitigation. These templates streamline data collection, track remediation progress, and generate comprehensive reports for stakeholders, enhancing decision-making processes. Utilizing such templates improves consistency, accuracy, and productivity in vulnerability management efforts critical to protecting organizational assets.
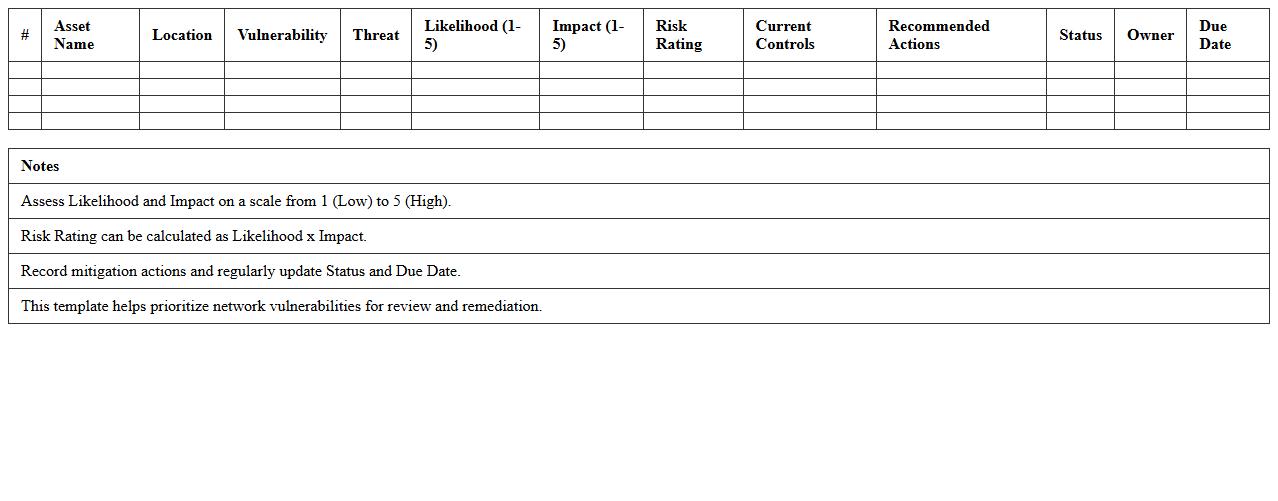
Network Vulnerability Risk Assessment Excel Template
A
Network Vulnerability Risk Assessment Excel Template is a structured document designed to identify, analyze, and prioritize security weaknesses within a network infrastructure. It helps IT professionals systematically evaluate potential threats, assess the impact and likelihood of vulnerabilities, and implement appropriate mitigation strategies. This template streamlines risk management processes by providing a clear framework to track findings and improve overall network security posture efficiently.
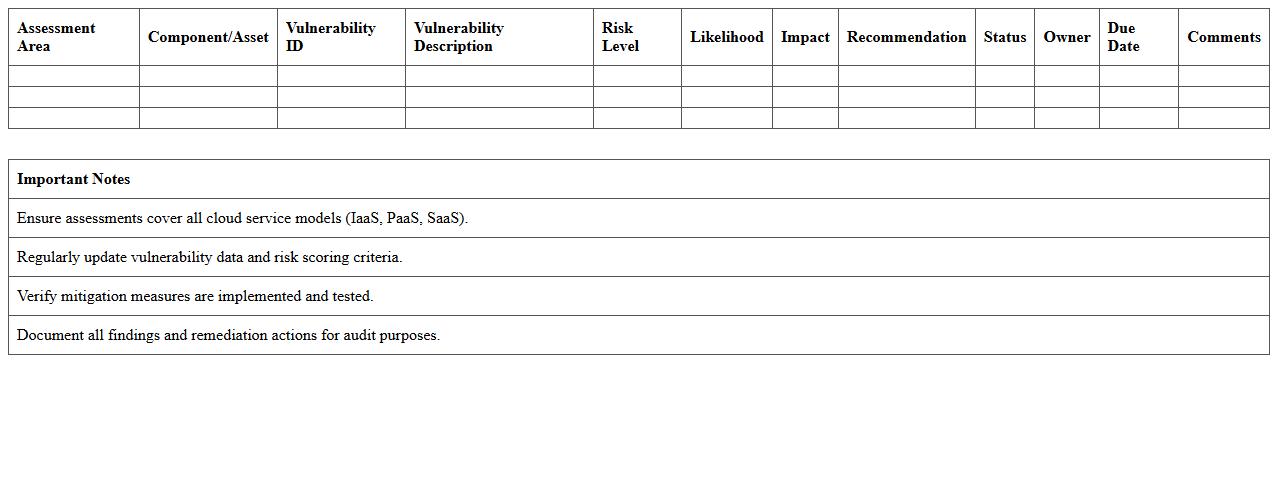
Web Application Vulnerability Audit Excel Template
The
Web Application Vulnerability Audit Excel Template document is a structured tool designed to systematically identify, record, and analyze security weaknesses within web applications. It helps cybersecurity professionals and developers track potential risks such as SQL injection, cross-site scripting (XSS), and insecure authentication mechanisms in a clear, organized format. By leveraging this template, teams can prioritize remediation efforts, ensure comprehensive vulnerability coverage, and enhance overall application security management.
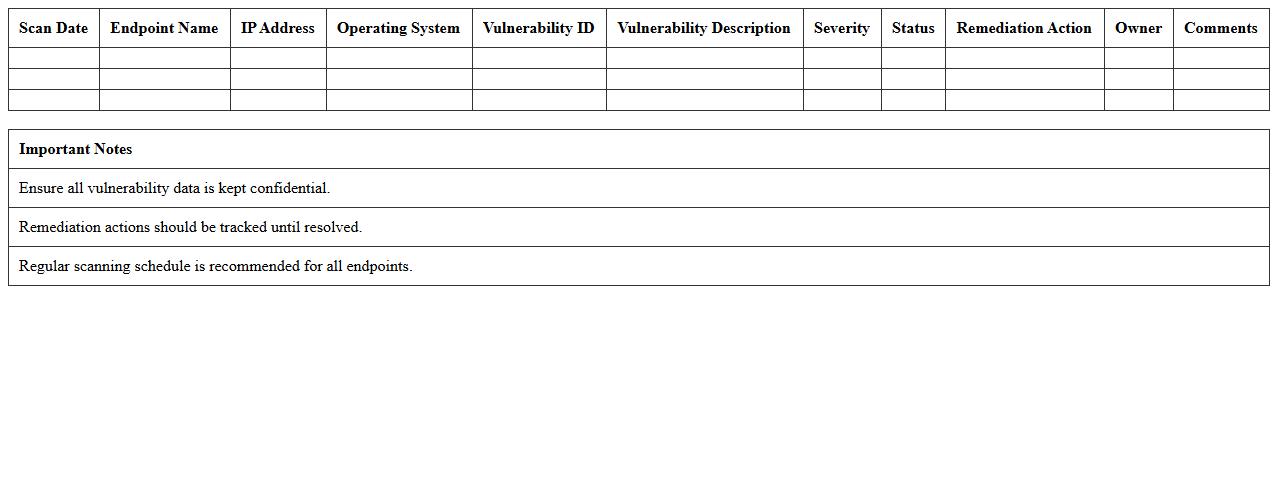
Endpoint Security Vulnerability Scan Results Template
The
Endpoint Security Vulnerability Scan Results Template document organizes and details findings from security scans performed on endpoints, identifying weaknesses such as outdated software, misconfigurations, and unpatched vulnerabilities. This template standardizes reporting to ensure clear communication between cybersecurity teams and stakeholders, facilitating rapid prioritization and remediation of risks. Utilizing this document supports improved endpoint protection strategies by providing actionable insights into security posture and compliance status.
Patch Management Vulnerability Tracking Excel Sheet
A
Patch Management Vulnerability Tracking Excel Sheet document is a structured spreadsheet used to identify, record, and monitor software vulnerabilities and patch deployment status across an organization's IT infrastructure. It helps IT teams systematically track missing patches, prioritize critical updates, and ensure timely remediation to reduce security risks. By consolidating vulnerability data and patch information in one place, it enhances visibility, compliance, and operational efficiency in managing software security.
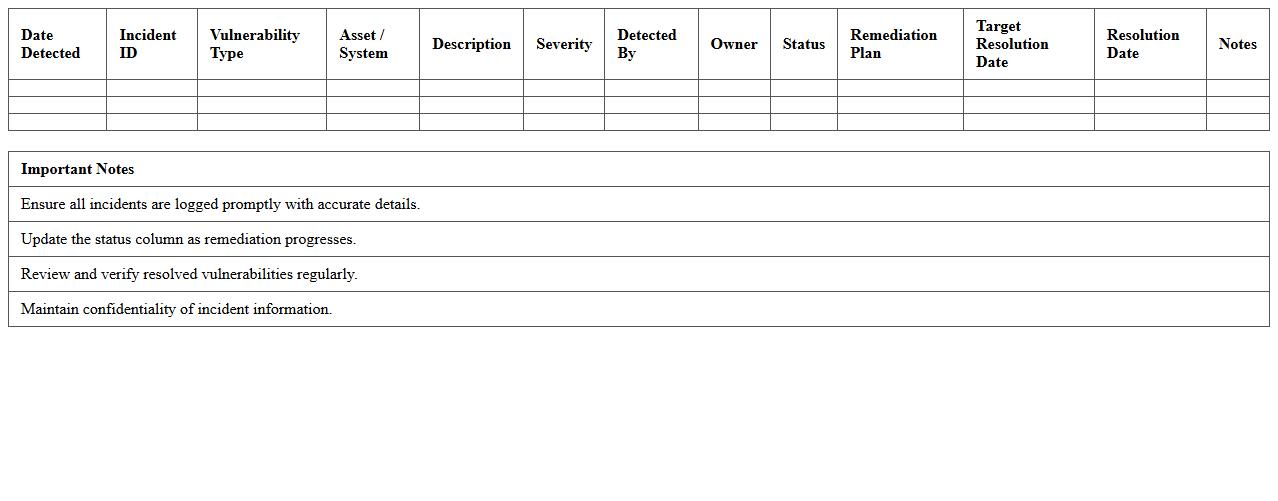
Security Incident Vulnerability Findings Log Excel
The
Security Incident Vulnerability Findings Log Excel document systematically records detected security weaknesses and incident details to facilitate thorough analysis and tracking. It enables organizations to prioritize remediation efforts by categorizing vulnerabilities based on severity, impact, and occurrence frequency. This log serves as a critical tool for continuous monitoring, compliance reporting, and improving overall cybersecurity posture.
Cloud Infrastructure Vulnerability Assessment Template
A
Cloud Infrastructure Vulnerability Assessment Template document provides a structured framework to identify, evaluate, and prioritize security weaknesses within cloud environments. This template streamlines the process of assessing risks associated with virtual machines, networks, storage, and applications, ensuring comprehensive coverage of potential vulnerabilities. Using this template helps organizations proactively strengthen their cloud security posture and minimize the chances of data breaches or service disruptions.
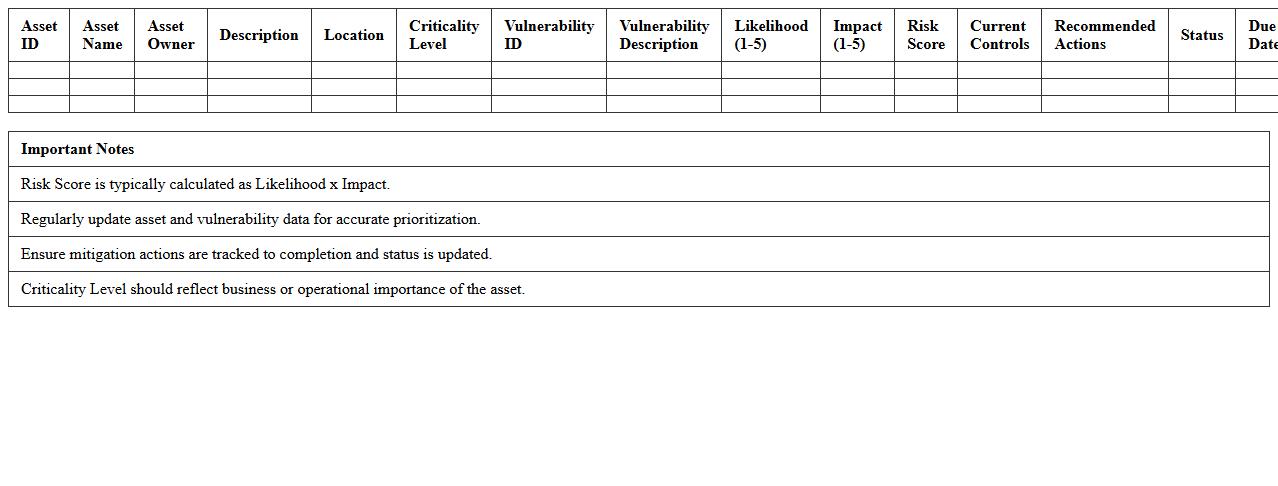
Critical Asset Vulnerability Prioritization Excel Sheet
The
Critical Asset Vulnerability Prioritization Excel Sheet is a structured tool designed to systematically identify and rank vulnerabilities within key organizational assets based on risk and potential impact. By organizing data related to asset importance, threat likelihood, and vulnerability severity, it enables focused resource allocation for security improvements. This document enhances decision-making by highlighting critical areas that require immediate attention to strengthen overall risk management strategies.
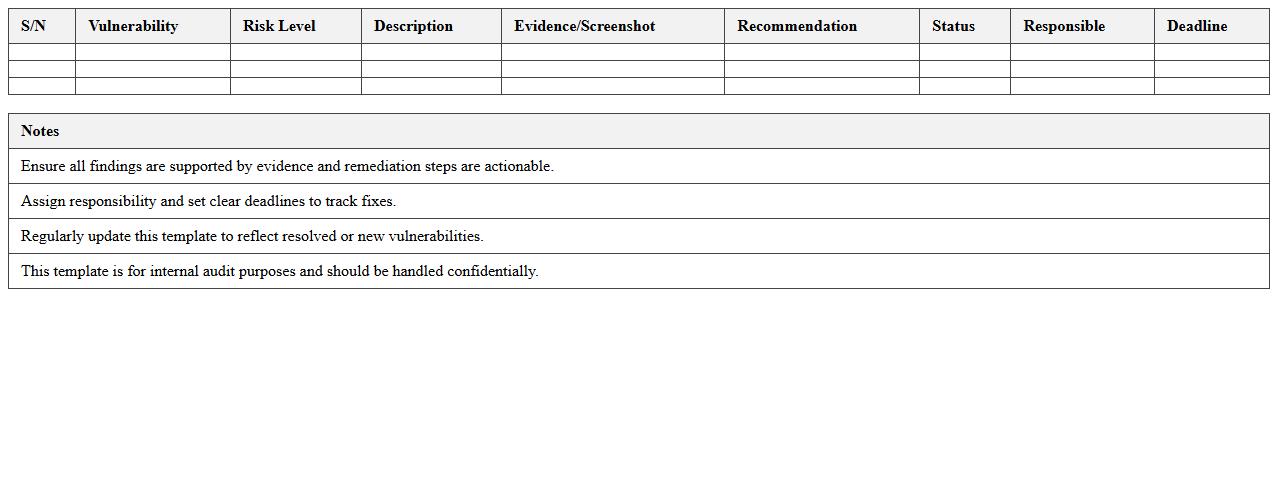
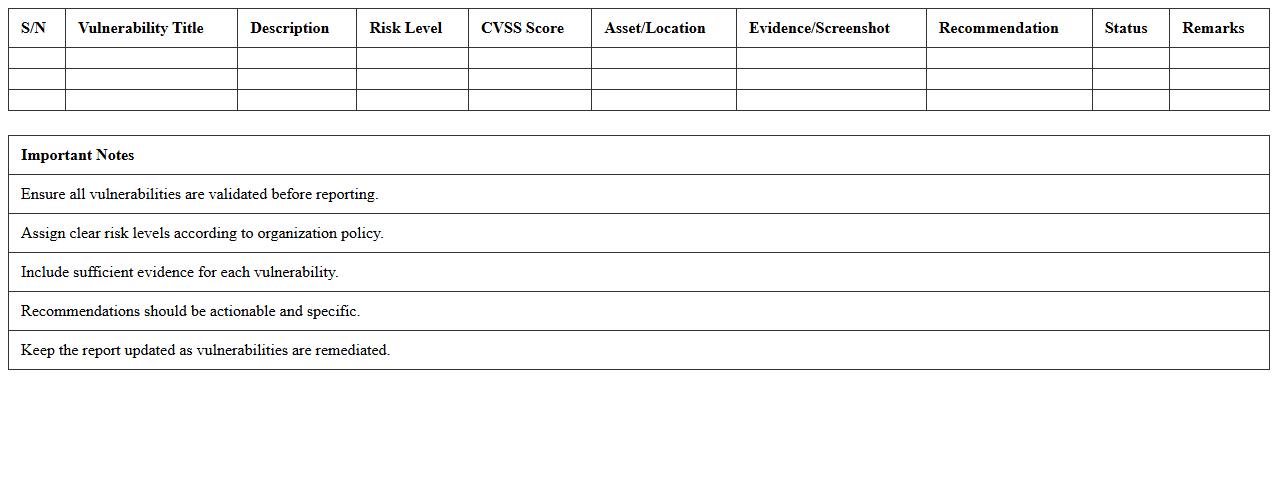
Penetration Test Vulnerability Report Excel Template
The
Penetration Test Vulnerability Report Excel Template document organizes and details security weaknesses identified during penetration testing, allowing cybersecurity professionals to systematically track, assess, and prioritize vulnerabilities. It enhances clarity by providing structured columns for vulnerability descriptions, risk ratings, remediation status, and responsible teams, facilitating effective communication between technical and management stakeholders. This template streamlines the remediation process and supports compliance with security standards by maintaining a comprehensive record of identified threats and corrective actions.
Vulnerability Remediation Action Plan Tracking Excel
A
Vulnerability Remediation Action Plan Tracking Excel document systematically records identified security flaws, assigned responsibilities, deadlines, and remediation progress, providing a clear overview of the mitigation process. It enhances organizational cybersecurity by ensuring timely tracking and resolution of vulnerabilities, reducing risk exposure to potential threats. This tool improves collaboration and accountability among IT teams, enabling efficient resource allocation and compliance with security policies.
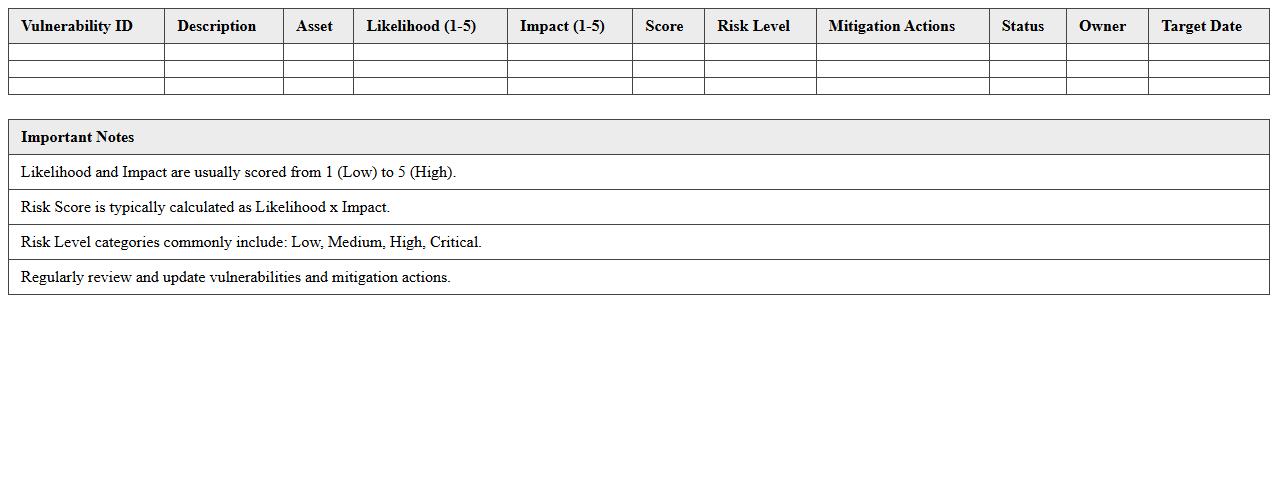
Vulnerability Scoring and Risk Matrix Excel Template
A
Vulnerability Scoring and Risk Matrix Excel Template document is a structured tool used to assess and quantify security vulnerabilities by assigning scores based on their severity, likelihood, and impact. This template helps organizations prioritize risks efficiently, enabling targeted mitigation strategies and resource allocation. By visualizing risks through a matrix format, it enhances decision-making processes for cybersecurity management and compliance tracking.
Which key metrics are auto-calculated in the Vulnerability Assessment Excel template?
The template auto-calculates critical metrics such as total vulnerabilities, remediation status, and risk scores. It includes dynamic summaries that update based on input data for comprehensive tracking. These calculations help streamline the vulnerability management process by providing clear insights instantly.
How are risk ratings visually represented for rapid executive review?
Risk ratings are visually displayed using color-coded heatmaps and conditional formatting in the Excel template. High, medium, and low risks are easily distinguished by red, orange, and green color gradients respectively. This visual aid ensures executives can quickly assess security posture at a glance.
Does the Excel support integration with third-party vulnerability scanning tools?
The template supports importing data from popular third-party vulnerability scanning tools via CSV or XLSX file formats. While direct live integration may not be available, the Excel design allows for seamless data updates from external sources. This flexibility enhances the utility of the assessment process in varied environments.
What formulas are used to prioritize remediation tasks in the worksheet?
Formulas combine vulnerability severity, asset criticality, and exploit availability into a composite risk score for prioritization. Weighted calculations identify the highest priority remediation tasks to ensure efficient resource allocation. These formulas dynamically update as new vulnerability data is entered.
Can custom asset categories be added for specific client environments?
The Excel template allows users to add and customize asset categories tailored to unique client environments. This feature enables detailed risk assessments reflective of various industries or infrastructure types. Custom categories improve the relevance and accuracy of the vulnerability evaluation.