IT Security Risk Assessment Checklist Excel Template
The
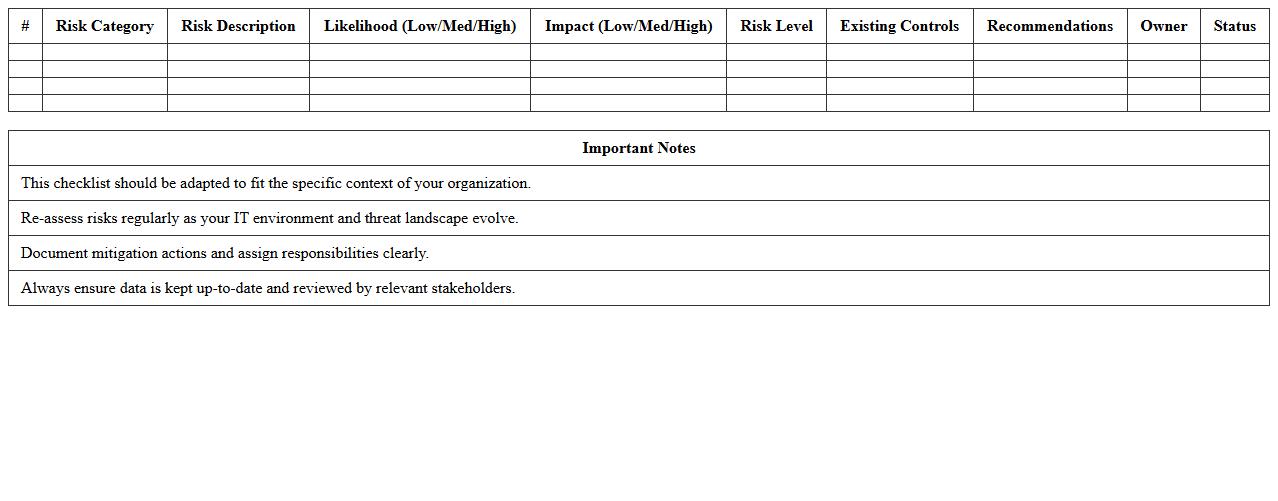
IT Security Risk Assessment Checklist Excel Template document is a structured tool designed to identify, evaluate, and prioritize potential security threats within an organization's IT infrastructure. It provides a systematic approach to document vulnerabilities, assess their impact, and implement mitigation strategies, enhancing cybersecurity management. This template is useful for maintaining compliance, improving risk visibility, and streamlining decision-making processes in IT security operations.
Corporate Network Vulnerability Assessment Excel Spreadsheet
A
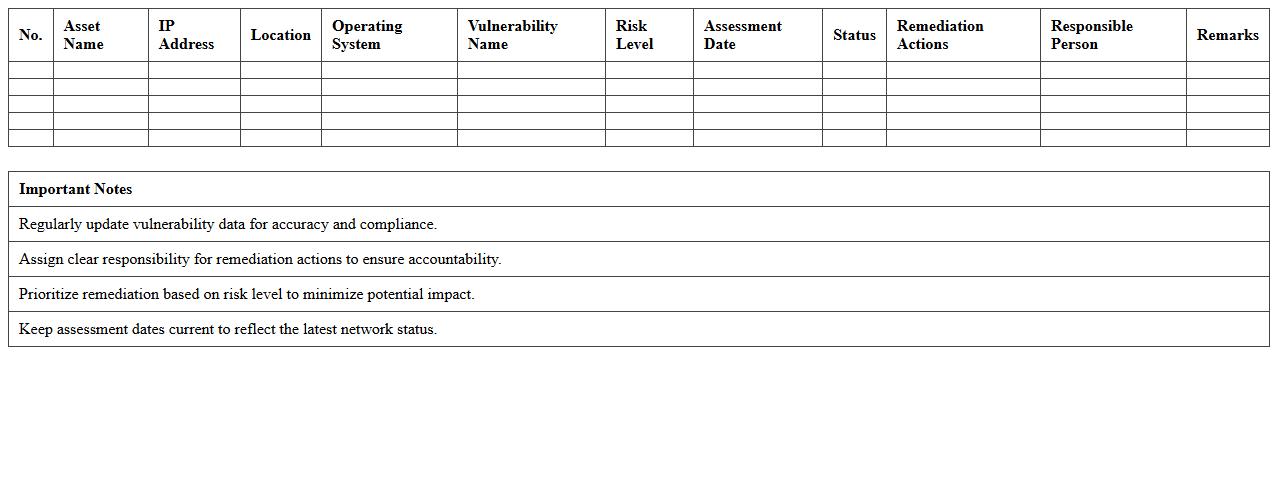
Corporate Network Vulnerability Assessment Excel Spreadsheet document systematically organizes and analyzes potential security weaknesses within an organization's network infrastructure. It allows IT professionals to track identified vulnerabilities, prioritize remediation efforts based on risk levels, and maintain comprehensive records of security assessments. This tool enhances the effectiveness of cybersecurity strategies by providing clear visibility into network security gaps and facilitating data-driven decision-making.
Cybersecurity Gap Analysis Excel Template
The
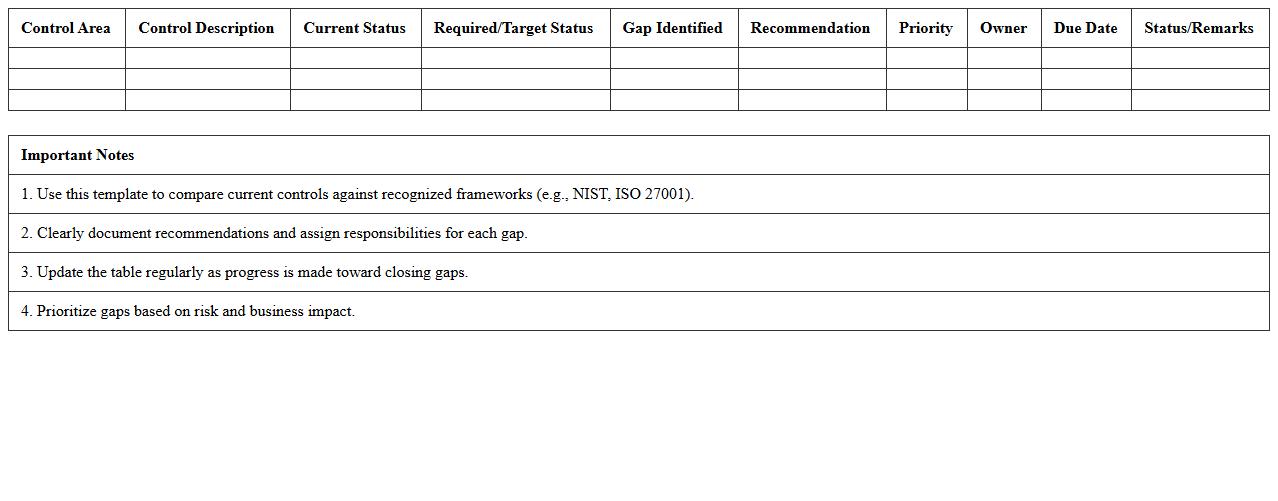
Cybersecurity Gap Analysis Excel Template document serves as a structured tool to identify and evaluate discrepancies between an organization's current cybersecurity posture and desired standards or compliance requirements. By systematically comparing existing controls against best practices or regulatory frameworks, it helps prioritize vulnerabilities and allocate resources effectively. This template streamlines risk management processes, enhances security planning, and supports continuous improvement initiatives within an organization.
IT Compliance Audit Tracking Excel Sheet
An
IT Compliance Audit Tracking Excel Sheet is a structured document designed to monitor and record the status of IT compliance requirements, controls, and audit findings. It helps organizations systematically track regulatory adherence, identify gaps, and manage remediation efforts effectively. By consolidating audit data in one place, this tool enhances transparency, accountability, and simplifies the reporting process for IT governance teams.
Network Security Controls Inventory Excel Template
The
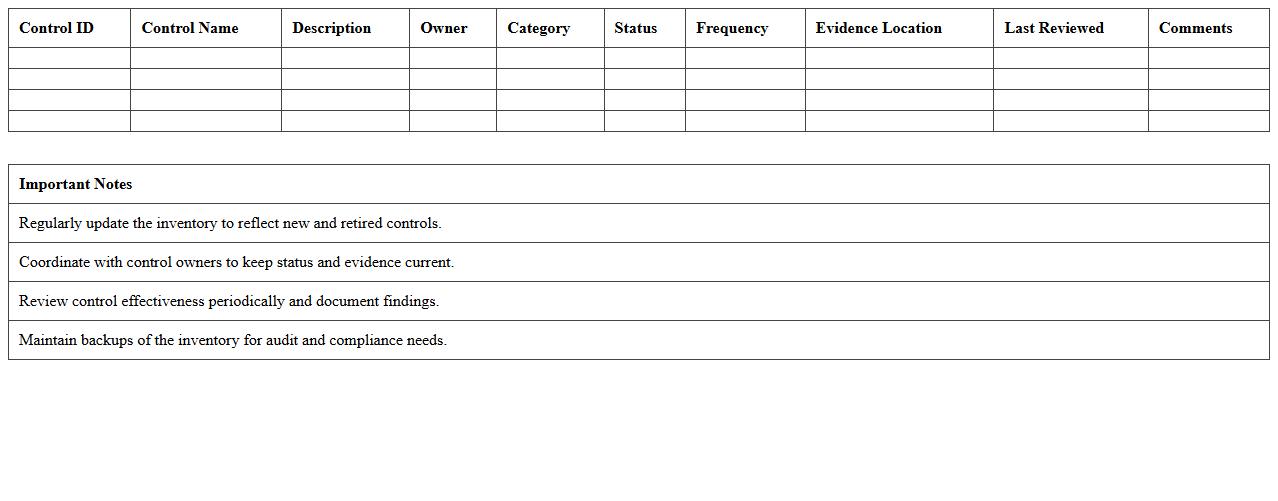
Network Security Controls Inventory Excel Template is a structured document designed to catalog and track various security measures implemented across a network. It helps organizations systematically identify, assess, and manage controls such as firewalls, intrusion detection systems, and access policies, ensuring comprehensive protection against cyber threats. This template streamlines auditing processes, enhances compliance with industry standards, and supports continuous security improvement by providing clear visibility into the existing network defenses.
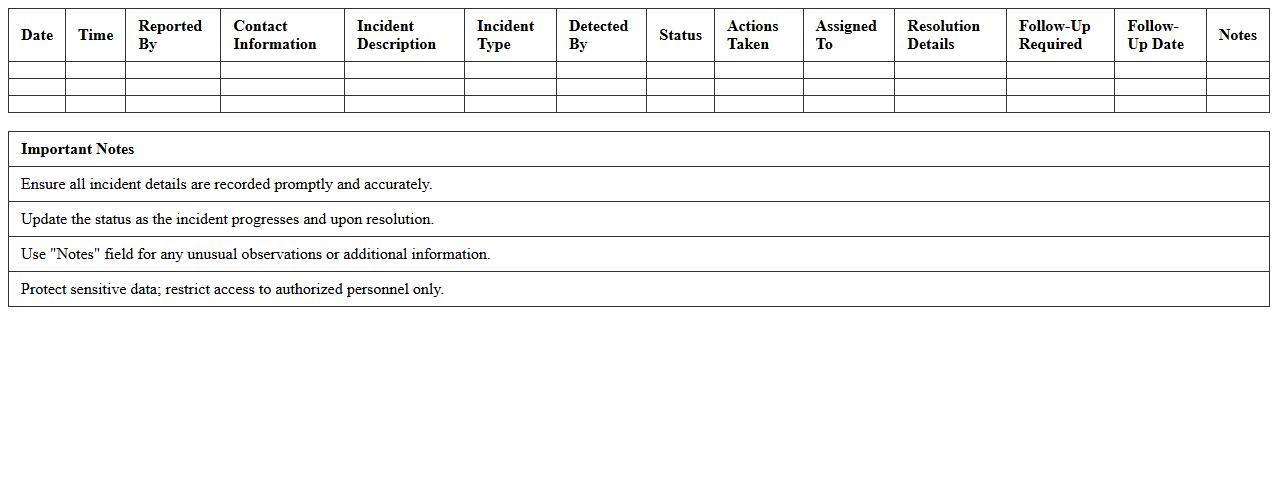
Incident Response Log Excel Format
An
Incident Response Log Excel Format document is a structured spreadsheet designed to systematically record and track security incidents, detailing timestamps, incident types, affected systems, actions taken, and the personnel involved. This format enhances organization by enabling efficient data entry, real-time updates, and clear visibility of incident progression for cybersecurity teams. Using this log helps improve incident handling, ensures compliance with reporting standards, and supports post-incident analysis for better future prevention.
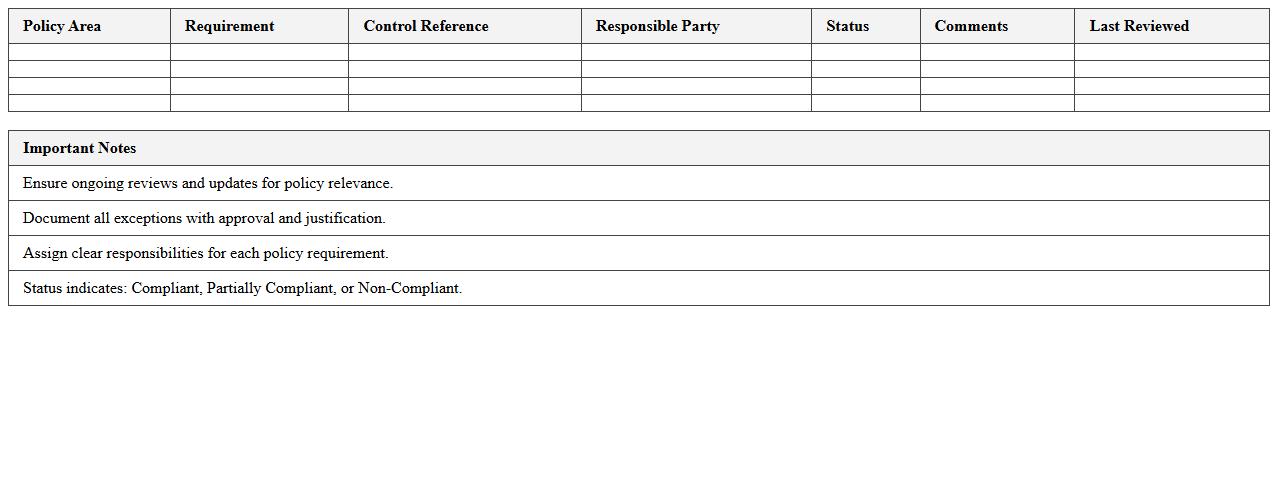
Information Security Policy Compliance Matrix Excel
The
Information Security Policy Compliance Matrix Excel document serves as a structured tool to map organizational policies against regulatory requirements, controls, and compliance standards. It enables clear tracking of compliance status, identifying gaps and remediation efforts effectively. This matrix streamlines audits and enhances risk management by ensuring all information security policies align with industry benchmarks and legal mandates.
Security Patch Management Tracker Excel Template
The
Security Patch Management Tracker Excel Template is a structured document designed to monitor and manage the deployment of security patches across an organization's IT infrastructure. It helps systematically track patch statuses, installation dates, and compliance levels, ensuring vulnerabilities are addressed promptly to protect against cyber threats. Using this template enhances visibility into patch management processes, reduces the risk of security breaches, and supports regulatory compliance efforts.
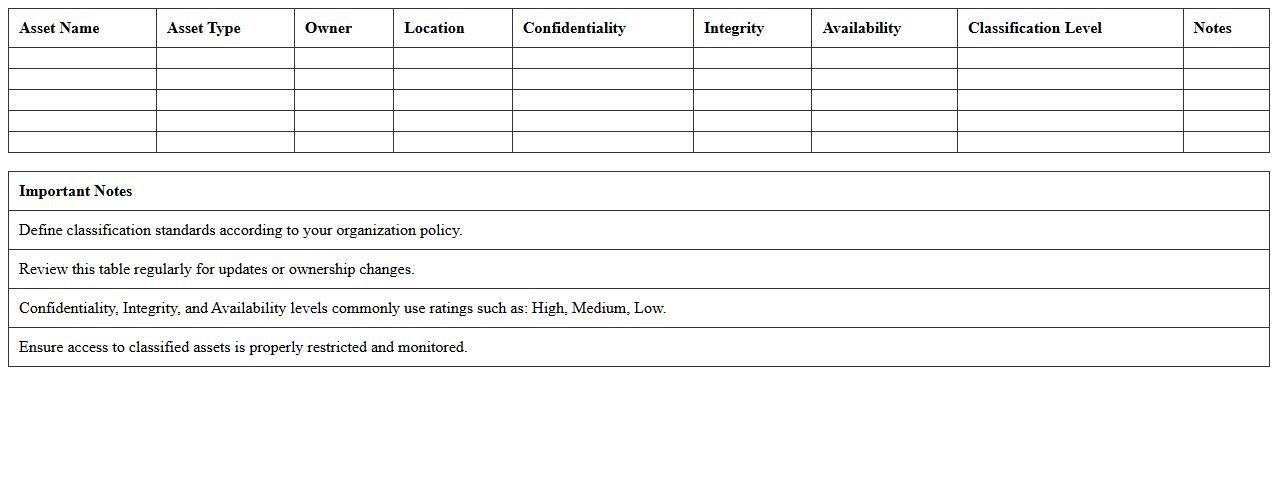
IT Asset Security Classification Excel Spreadsheet
An
IT Asset Security Classification Excel Spreadsheet document categorizes digital and physical technology assets based on their sensitivity, value, and risk level, allowing organizations to manage security policies effectively. This tool aids in identifying critical assets requiring higher protection, ensuring compliance with regulatory standards, and streamlining risk management processes. By maintaining a clear inventory with classification levels, it supports informed decision-making and prioritizes resource allocation for cybersecurity measures.
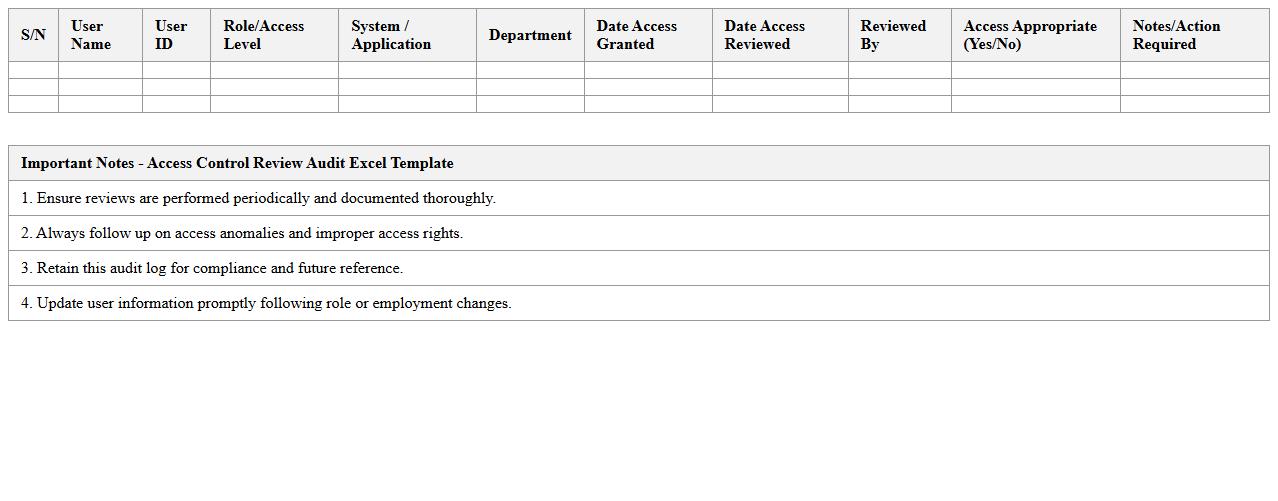
Access Control Review Audit Excel Template
The
Access Control Review Audit Excel Template document is a structured tool designed to systematically evaluate and document access permissions across systems and applications. It helps identify unauthorized access, ensure compliance with security policies, and track necessary corrective actions efficiently. By organizing access data clearly, this template simplifies audit processes and enhances overall security governance.
Which encryption standards are documented for protecting sensitive data in the IT Security Assessment Excel?
The IT Security Assessment Excel emphasizes the use of AES (Advanced Encryption Standard) for protecting sensitive data. It also highlights the importance of implementation of TLS (Transport Layer Security) for data in transit encryption. These standards ensure robust data confidentiality and integrity across IT systems.
Does the letter specify vulnerability scanning intervals for corporate network assets?
The letter explicitly mandates regular vulnerability scanning for corporate network assets. It recommends conducting scans at intervals not exceeding 30 days to promptly identify and address security weaknesses. Consistent scanning is critical for maintaining a proactive security posture.
Are third-party access controls and logging requirements addressed in the assessment document?
The assessment document thoroughly addresses third-party access controls to ensure external vendors follow strict security protocols. It mandates detailed logging of all third-party activities to provide accountability and traceability. These measures prevent unauthorized access and enhance overall security governance.
How does the letter outline incident response documentation within the Excel assessment?
The letter outlines clear incident response documentation procedures within the Excel assessment framework. It specifies that each incident must be logged with timelines, actions taken, and resolution status. This structured documentation supports timely incident mitigation and post-event analysis.
Is there a section detailing security compliance mappings (e.g., ISO 27001, NIST) in the document?
Yes, the document includes a dedicated section for security compliance mappings that aligns organizational controls with standards like ISO 27001 and NIST. This section aids in tracking adherence to industry benchmarks and regulatory requirements. Compliance mapping ensures a comprehensive risk management strategy.